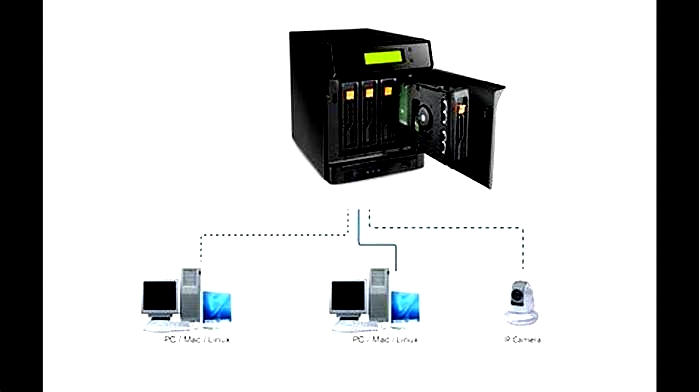
Tutorial Building a Custom NAS Network Attached Storage System
Sorry, your request has been blocked
This request has been blocked by BigScoots web application firewall (WAF) because it has raised security concerns.
When a request includes information or metadata identified as a security risk, the BigScoots WAF will stop those requests from reaching your website as a security measure to protect it from potential cyber criminal activities.
Another reason may be that the website owner has placed a block or restriction on specific users from accessing their website due to internal reasons.
If you are a website visitor and feel you have gotten this message in error, please contact the website owner directly.
If you are the website owner and certain that you are not supposed to see this error page, then please click on the button below to get in touch with the support team and we will take a deeper look into it.
Contact SupportPlease mention the "Ray ID" and "Client IP" (as shown below) to your ticket.
How To Build Network Attached Storage
Introduction
Welcome to the world of Network Attached Storage (NAS), where the convenience of centralized storage meets the accessibility of a network connection. Whether you are a home user looking to consolidate your media files or a business in need of a reliable data storage solution, building your own NAS can be a rewarding and cost-effective endeavor. By following this guide, you will learn the essential steps to create a custom NAS tailored to your specific needs.
Building a NAS allows you to have complete control over the hardware, software, and security measures, ensuring that your data is stored and accessed in a manner that aligns with your requirements. From selecting the right hardware components to configuring the storage and securing the network, this comprehensive guide will walk you through each stage of the process, empowering you to create a robust and efficient NAS system.
Whether you are a tech enthusiast seeking a DIY project or a professional aiming to optimize data management, the journey to building your own NAS begins with understanding the fundamental aspects of hardware selection, operating system choices, network setup, and security measures. By the end of this guide, you will have the knowledge and confidence to embark on this exciting venture and build a reliable NAS that caters to your unique storage needs.
Choosing the Right Hardware
When embarking on the journey of building a Network Attached Storage (NAS) system, selecting the right hardware is a crucial first step. The hardware components you choose will determine the performance, capacity, and scalability of your NAS, so its essential to make informed decisions based on your specific storage requirements.
1. Processor and Memory: The heart of your NAS is the processor, which dictates the systems overall performance. Opt for a processor with multiple cores and a high clock speed to handle concurrent read/write operations efficiently. Additionally, ample memory is essential for smooth multitasking and data caching, so consider installing at least 4GB of RAM, with room for future expansion.
2. Storage Drives: The choice of storage drives significantly impacts the NASs capacity, speed, and data redundancy. Select high-capacity hard disk drives (HDDs) or solid-state drives (SSDs) based on your storage needs and performance expectations. For data redundancy and protection against drive failures, consider implementing a RAID (Redundant Array of Independent Disks) configuration using multiple drives.
3. Network Interface: A Gigabit Ethernet interface is a minimum requirement for a NAS, offering sufficient bandwidth for data transfer over the network. For higher performance and future-proofing, consider a NAS with multiple Gigabit Ethernet ports or even 10 Gigabit Ethernet support, especially if you anticipate heavy network usage.
4. Expansion Slots and USB Ports: Evaluate the availability of expansion slots for adding more storage or networking capabilities in the future. Additionally, having multiple USB ports enables easy connectivity for external storage devices, printers, or UPS (Uninterruptible Power Supply) units, enhancing the NASs versatility.
5. Power Supply and Cooling: A reliable power supply unit with adequate wattage and efficient cooling mechanisms are essential for maintaining the stability and longevity of your NAS system. Opt for a power supply with ample headroom to accommodate additional drives and expansion cards, and ensure that the NAS enclosure provides sufficient airflow to prevent overheating.
By carefully considering these hardware aspects and aligning them with your storage goals, you can lay a solid foundation for your NAS build, setting the stage for the subsequent steps in the construction process.
Selecting the Operating System
Once you have determined the hardware components for your Network Attached Storage (NAS) system, the next critical decision involves selecting the appropriate operating system (OS) to power your NAS. The OS serves as the backbone of the NAS, providing the necessary tools and interfaces for managing storage, network connectivity, and user access. When choosing an OS for your NAS, consider the following key factors:
1. Purpose and User Interface: Evaluate the intended use of your NAS, whether its for personal file storage, media streaming, or business applications. Some OS options, such as FreeNAS and OpenMediaVault, are designed specifically for NAS environments, offering intuitive web-based interfaces for easy configuration and management.
2. File System Support: Different operating systems support various file systems, each with its own advantages in terms of performance, data integrity, and compatibility. Ensure that the OS you choose provides robust support for the file system of your storage drives, whether its ZFS, Btrfs, ext4, or others, to maximize the NASs capabilities.
3. Data Protection and Redundancy: Look for OS features that facilitate data protection and redundancy, such as snapshot capabilities, RAID management tools, and built-in backup utilities. These functionalities are crucial for safeguarding your data against hardware failures and ensuring continuous access to stored information.
4. Community Support and Updates: Opt for an OS with an active and responsive community, as this ensures ongoing support, frequent updates, and access to a wealth of user-contributed resources and plugins. Community-driven OS platforms often benefit from continuous improvements and a vibrant ecosystem of add-on applications.
5. Compatibility and Extensibility: Consider the compatibility of the OS with your chosen hardware components, including processor architecture, network interfaces, and expansion cards. Additionally, assess the extensibility of the OS through third-party plugins, Docker containers, or virtualization support to expand the NASs functionality as your needs evolve.
By carefully evaluating these factors and exploring the available OS options, you can make an informed decision that aligns with your specific storage requirements and technical preferences. The chosen OS will serve as the cornerstone of your NAS, shaping its capabilities and functionality as you proceed with the setup and configuration process.
Setting Up the Network
Establishing a robust and secure network infrastructure is a pivotal aspect of building a Network Attached Storage (NAS) system. The network configuration directly influences the accessibility, performance, and data transfer capabilities of the NAS, making it essential to pay close attention to this phase of the setup process. Here are the key steps involved in setting up the network for your NAS:
1. Network Topology: Determine the network topology that best suits your NAS deployment. Whether you opt for a simple peer-to-peer connection in a home environment or a more complex infrastructure with dedicated switches, routers, and VLANs in a business setting, understanding the network topology is crucial for efficient data flow and access control.
2. IP Addressing and DHCP: Configure static IP addresses for the NAS and other critical network devices to ensure consistent accessibility. Alternatively, leverage Dynamic Host Configuration Protocol (DHCP) for automatic IP assignment, taking into account the benefits of both approaches in terms of manageability and network stability.
3. Network Security: Implement robust security measures to safeguard the NAS from unauthorized access and potential threats. Utilize strong encryption protocols for data transmission, enable firewalls to filter network traffic, and consider setting up virtual private network (VPN) access for secure remote connectivity to the NAS.
4. Quality of Service (QoS): Prioritize network traffic by configuring Quality of Service settings to ensure optimal performance for NAS-related activities such as file transfers, media streaming, and remote access. QoS mechanisms help prevent network congestion and maintain consistent data throughput for critical NAS operations.
5. Remote Access and Cloud Integration: If remote access and cloud integration are integral to your NAS requirements, configure port forwarding on the router and explore NAS-specific cloud services or self-hosted solutions for seamless access to your data from anywhere, while upholding stringent security protocols.
By meticulously addressing these network setup considerations, you can establish a resilient and efficient network environment that forms the backbone of your NAS infrastructure. A well-designed network ensures seamless data transfer, reliable access to stored content, and robust security measures that protect your valuable data assets.
Configuring the Storage
Once the hardware and network components are in place, the next critical phase in building a Network Attached Storage (NAS) system involves configuring the storage to accommodate your data storage and access requirements. Proper storage configuration ensures optimal performance, data redundancy, and efficient utilization of the available storage capacity. Here are the essential steps for configuring the storage in your NAS:
1. Storage Pool Creation: Depending on the chosen operating system and file system, create storage pools that aggregate the capacity of multiple drives into a unified storage resource. This enables flexible allocation of storage space and facilitates the implementation of data protection mechanisms such as RAID configurations.
2. RAID Configuration: Implement a RAID level that aligns with your data protection and performance goals. Whether its RAID 1 for mirroring, RAID 5 for a balance of capacity and redundancy, or RAID 10 for a combination of striping and mirroring, select the appropriate RAID configuration to safeguard your data against drive failures and ensure continuous availability.
3. File System Optimization: Fine-tune the file system settings to optimize performance and data integrity. Configure parameters such as block sizes, caching options, and checksumming mechanisms based on the specific workload characteristics and access patterns of your NAS environment.
4. Storage Tiering and Caching: Explore the possibility of implementing storage tiering and caching mechanisms to enhance performance and responsiveness. By leveraging faster storage media as cache or creating tiered storage with varying performance levels, you can improve the overall data access speed and responsiveness of the NAS system.
5. Data Compression and Deduplication: If supported by the chosen operating system and file system, consider enabling data compression and deduplication to optimize storage utilization and reduce the overall storage footprint. These features can lead to significant space savings, especially when storing redundant or highly compressible data.
By meticulously configuring the storage components of your NAS, you can create a resilient and efficient storage environment that caters to your data storage, protection, and performance needs. The proper configuration of storage pools, RAID levels, file system settings, and advanced storage features ensures that your NAS operates optimally and delivers reliable access to your stored data.
Securing the Network Attached Storage
Securing your Network Attached Storage (NAS) is paramount to safeguarding sensitive data and ensuring the integrity of your storage environment. By implementing robust security measures, you can mitigate potential threats, prevent unauthorized access, and fortify the overall resilience of your NAS system. Here are essential steps for securing your NAS:
1. Access Control and User Permissions: Establish granular access controls and user permissions to regulate who can access specific folders, files, and system settings on the NAS. By configuring user accounts with appropriate privileges and implementing role-based access control, you can enforce strict data access policies and prevent unauthorized alterations.
2. Strong Authentication Mechanisms: Enforce strong authentication practices by requiring complex passwords, implementing multi-factor authentication, and regularly updating user credentials. Additionally, consider integrating the NAS with centralized authentication services such as LDAP or Active Directory for streamlined user management and enhanced security.
3. Encryption of Data in Transit and at Rest: Utilize robust encryption protocols to secure data both during transmission over the network and while at rest on the storage drives. Implementing protocols such as SSL/TLS for network communication and full-disk encryption for stored data provides an additional layer of protection against unauthorized interception and access.
4. Regular Software Updates and Patch Management: Stay vigilant about applying software updates and security patches for the NAS operating system and associated applications. Timely updates help address known vulnerabilities and ensure that the NAS remains resilient against emerging security threats and exploits.
5. Intrusion Detection and Monitoring: Deploy intrusion detection systems and network monitoring tools to detect and respond to unauthorized access attempts, unusual network behavior, or potential security breaches. By actively monitoring the NAS environment, you can swiftly identify and mitigate security incidents before they escalate.
6. Backup and Disaster Recovery Planning: Implement robust backup strategies to create redundant copies of critical data and ensure the availability of recovery mechanisms in the event of data loss or system compromise. Regularly test the backup and recovery processes to validate their effectiveness and reliability.
By diligently implementing these security measures, you can fortify your NAS against a wide range of security threats and vulnerabilities, fostering a secure storage environment that instills confidence in the integrity and confidentiality of your stored data.
Conclusion
Congratulations on embarking on the journey to build your own Network Attached Storage (NAS) system. Throughout this guide, youve delved into the essential aspects of hardware selection, operating system choices, network setup, storage configuration, and security measures, gaining valuable insights into the intricate process of creating a custom NAS tailored to your specific needs.
By carefully choosing the right hardware components, including a robust processor, ample memory, reliable storage drives, and network interfaces, youve laid a solid foundation for a high-performance NAS. The selection of an operating system that aligns with your storage goals and technical preferences has empowered you to harness the full potential of your NAS, providing a rich set of tools and features for storage management and data access.
Setting up a resilient network infrastructure, configuring the storage with optimal performance and redundancy, and implementing stringent security measures have collectively fortified your NAS against potential threats and vulnerabilities, ensuring the integrity and confidentiality of your stored data.
As you conclude this guide, you now possess the knowledge and confidence to embark on the exciting venture of building a reliable NAS that caters to your unique storage requirements. Whether you are a home user consolidating media files or a business optimizing data management, the journey to build your own NAS has equipped you with the expertise to create a robust and efficient storage solution.
Remember that the process of building a NAS is not merely a technical endeavor; its a testament to your ability to craft a storage environment that reflects your specific needs and preferences. Your NAS stands as a testament to your dedication to data management and your commitment to ensuring that your stored content is accessible, secure, and resilient.
As you move forward with your NAS project, continue to explore new technologies, stay informed about emerging storage trends, and adapt your NAS environment to accommodate evolving storage demands. Embrace the journey of building and maintaining a NAS, and revel in the satisfaction of owning a storage solution that empowers you to manage and access your data with unparalleled flexibility and control.