Securing Your Smart Home Network Implementing Firewalls Encryption and Guest Access Controls
Network Hardening: Best Practices & Techniques
Network hardening is a crucial aspect of enhancing security measures within an organizations digital infrastructure. Conducting vulnerability assessments and implementing strong communications protocols that encrypt sensitive data are essential in protecting against potential technology threats.
By implementing strong security controls and solutions, organizations can strengthen their network and protect themselves against security vulnerabilities, unauthorized access, and potential cyber attacks. This is an essential part of any effective security strategy.
What is Network Hardening?
Network hardening involves implementing various security protocols and measures to fortify the networks defenses and safeguard sensitive data.
This includes conducting vulnerability assessments to identify potential weaknesses, securing open ports, and utilizing the latest technology. Following these recommendations can significantly enhance network security.
In todays interconnected world, security vulnerabilities and the need for robust security controls have become increasingly important. Network hardening is a key component of any comprehensive security strategy to protect against cyber threats.
By implementing effective security solutions, organizations can ensure the integrity and confidentiality of their information. Network security strategies encompass a range of practices such as implementing firewalls, intrusion detection systems, access controls, encryption techniques, and server hardening.
These security controls, including system hardening and application hardening, collectively create layers of protection that make it significantly more challenging for malicious actors to compromise the network.
By prioritizing network hardening and implementing robust security controls, organizations demonstrate their commitment to maintaining a secure digital environment. Implementing strong security controls and network security strategies is crucial for hardening network security.
This not only prevents data breaches and unauthorized access attempts but also boosts confidence among clients and stakeholders who rely on the organizations ability to protect sensitive information.
Understanding Systems Hardening
Systems hardening is a crucial aspect of network security that focuses on securing individual devices. By implementing security controls and specific network security strategies, systems hardening aims to minimize vulnerabilities and enhance the overall resilience of a system. These measures also include ensuring secure network access.
Removing unnecessary software and services
One important step in systems hardening is removing unnecessary software and services from devices to ensure network access is secure. System hardening is crucial for hardening network security.
This process reduces the potential attack surface by reducing the number of applications, thereby minimizing entry points for hackers. Unnecessary software can include outdated or unused programs that may contain vulnerabilities or weak security protocols.
Configuring systems to minimize vulnerabilities
Another key aspect of systems hardening involves configuring devices to minimize vulnerabilities. Implementing strong passwords, enabling encryption, and regularly updating software and firmware are essential steps in hardening network security.
By hardening network security, potential weaknesses are addressed, making it harder for attackers to exploit them.
Enhancing overall system resilience
Systems hardening significantly enhances the overall resilience of a system by reducing its susceptibility to attacks. When devices undergo the process of hardening network security, they become more resilient against a range of threats including malware infections, unauthorized access attempts, and data breaches.
This helps ensure the integrity and availability of critical resources within the network.
Implementing systems hardening measures has several benefits:
Improved security: Systems hardening strengthens the security posture of individual devices by minimizing potential vulnerabilities.
Reduced risk: By hardening network security and removing unnecessary software and services, the attack surface is reduced, decreasing the likelihood of successful cyberattacks.
Enhanced performance: Streamlining device configurations can improve their performance by eliminating resource-draining processes or unnecessary background services.
Compliance adherence: Many industries have specific compliance regulations that require organizations to implement robust security measures. Systems hardening assists in meeting these requirements.
Protection against zero-day exploits: Zero-day exploits refer to vulnerabilities unknown to vendors or developers. Systems hardening practices help mitigate such risks by implementing general security best practices.
It is essential to note that while systems hardening provides valuable protection, it is not a foolproof solution.
Cybersecurity is an ongoing process that requires constant adaptation and monitoring. Regular updates, patches, and vulnerability assessments are necessary to stay ahead of emerging threats.
Exploring Network Security Techniques
Encryption Ensures Secure Data Transmission
Encryption is a crucial network security strategy that ensures secure data transmission. It involves encoding information in such a way that only authorized parties can access and understand it.
By encrypting data, even if it falls into the wrong hands, it remains unreadable and useless.
Pros:
Protects sensitive information from unauthorized access.
Safeguards data during transmission, reducing the risk of interception.
Provides an additional layer of security against malicious actors.
Cons:
Encryption can introduce some performance overhead due to the computational resources required for encryption and decryption.
If encryption keys are lost or compromised, it can lead to permanent loss of encrypted data.
RELATED: Why Encryption is Important: Protecting your Business Data in the Digital Age
Intrusion Detection Systems Identify Potential Threats
Intrusion Detection Systems (IDS) play a vital role in network security by identifying potential threats and suspicious activities within a network. These systems monitor network traffic and analyze it for any signs of unauthorized access or malicious behavior.
Pros:
Helps detect and respond to potential attacks promptly.
Provides real-time alerts about suspicious activities.
Enhances overall network security by actively monitoring for threats.
Cons:
IDS may generate false positives, resulting in unnecessary alerts.
Requires regular updates and maintenance to stay effective against emerging threats.
RELATED: Intrusion Detection Systems (IDS): What is an IDS, and how does it protect Businesses?
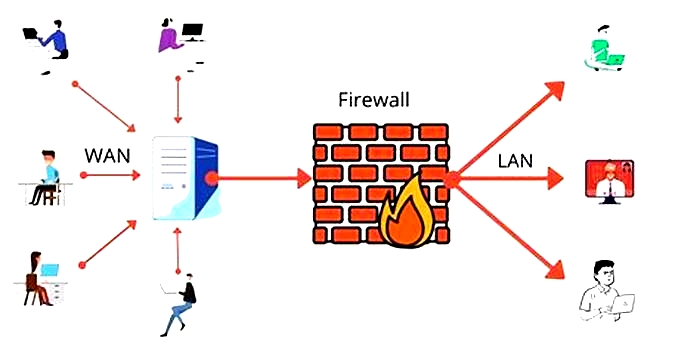
Firewalls Filter Network Traffic for Added Protection
Firewalls act as a barrier between internal networks and external networks or the internet. They filter incoming and outgoing network traffic based on predefined rules, effectively protecting against unauthorized access and blocking potentially harmful content.
Pros:
Prevents unauthorized access to the network.
Filters out malicious traffic, such as malware or phishing attempts.
Can be customized to enforce specific security policies based on organizational needs.
Cons:
RELATED: Network Security 101: Network Firewall Best Practices all Businesses must follow
Virtual Private Networks Create Secure Connections
Virtual Private Networks (VPNs) establish secure connections between remote users or networks and the organizations internal network. By encrypting data and routing it through a secure tunnel, VPNs provide an added layer of security for remote access.
Pros:
Encrypts data during transmission, protecting against interception.
Allows secure remote access to organizational resources.
Enhances privacy by masking the users IP address.
Cons:
RELATED: Site-to-Site VPN: What is a Site to Site VPN, and does my business need one?
Best Practices for Network Hardening
Regularly update software and firmware for security patches
To ensure the security of your network, it is crucial to regularly update your software and firmware with the latest security patches. These updates often contain fixes for vulnerabilities that could be exploited by hackers. By keeping your systems up to date, you can significantly reduce the risk of unauthorized access and data breaches.
Some key recommendations for updating software and firmware include:
Enable automatic updates whenever possible, so you dont have to rely on manual intervention.
Regularly check for updates from trusted sources such as software vendors or device manufacturers.
Prioritize critical security patches and install them promptly to address any known vulnerabilities.
Consider using vulnerability management tools that can help automate the process of identifying and applying necessary updates.
Implement strong passwords and multi-factor authentication
One of the simplest yet most effective ways to enhance network security is by implementing strong passwords and multi-factor authentication (MFA). Weak passwords are easy targets for hackers, so its important to choose complex passwords that are difficult to guess.
Here are some guidelines for creating strong passwords:
Use a combination of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessable information like birthdates or common words.
Regularly change your passwords to minimize the risk of unauthorized access.
In addition to strong passwords, MFA adds an extra layer of protection by requiring users to provide additional verification factors such as a fingerprint or a unique code sent via SMS.
This significantly reduces the likelihood of unauthorized access even if a password is compromised.
RELATED: Infosec Best Practices: Implementing Effective Password Policies
Conduct regular vulnerability assessments and penetration testing
Regularly conducting vulnerability assessments and penetration testing is essential in identifying potential weaknesses in your network infrastructure. These assessments involve scanning your systems for vulnerabilities that could be exploited by attackers.
Key steps in conducting these assessments include:
Identify potential attack vectors: Determine how an attacker might gain unauthorized access to your network.
Scan for vulnerabilities: Use specialized tools to scan your systems and identify any vulnerabilities present.
Prioritize and remediate: Assess the severity of each vulnerability and prioritize fixing the most critical ones first.
By regularly performing these assessments, you can proactively address vulnerabilities before they are exploited by malicious actors.
RELATED:Mastering the Vulnerability Management Lifecycle
Establish a comprehensive incident response plan
Despite taking preventive measures, its important to acknowledge that security incidents may still occur. Having a well-defined incident response plan in place will help you effectively respond to and mitigate the impact of such incidents.
An incident response plan should include:
Clearly defined roles and responsibilities for team members involved in incident response.
Detailed steps to follow in the event of a security breach or other incidents.
Communication protocols for notifying relevant stakeholders, including customers or regulatory authorities if necessary.
Regularly test and update your incident response plan to ensure its effectiveness when needed most.
RELATED: Mastering Incident Response: Best Practices for Effective Handling
Implementing Access Controls for Networks
Access controls play a crucial role in network hardening by restricting user access and ensuring that only authorized individuals can access sensitive information. Lets explore some key strategies for implementing effective access controls to enhance the security of your network.
Restrict User Access Based on Roles and Permissions
One important aspect of network security is to restrict user access based on their roles and permissions. This means that users should only have access to the resources and data that are necessary for them to perform their job functions. By implementing role-based access control (RBAC), organizations can assign specific privileges and rules to different roles within the network.
Pros:
Reduces the risk of unauthorized access.
Ensures that users only have access to what they need, minimizing potential damage from insider threats.
Cons:
RELATED: Role-Based Access Control (RBAC): What is it, and how does it work?
Utilize Strong Authentication Methods like Biometrics or Tokens
Implementing strong authentication methods adds an extra layer of security by verifying the identity of users before granting them access to the network. Biometrics, such as fingerprint or iris scans, provide a unique identifier that cannot be easily replicated. Tokens, such as smart cards or USB devices, generate one-time passwords for secure login.
Pros:
Cons:
RELATED: The Benefits of 2-Factor Authentication: Enhancing Your Business Security
Monitor Network Activity with Audit Logs and Alerts
Monitoring network activity is vital for detecting any suspicious behavior or unauthorized access attempts. By maintaining detailed audit logs and setting up alerts, organizations can quickly identify any unusual activities within their networks.
Pros:
Cons:
RELATED: Network Monitoring: Recognizing the need for Monitoring your Network for Cybersecurity
Limit Physical Access to Critical Network Components
Physical access controls are equally important in network hardening. By restricting physical access to critical network components, organizations can prevent unauthorized individuals from tampering with or compromising the network infrastructure.
Pros:
Cons:
Implementing robust access controls is essential for protecting networks from unauthorized access and potential security breaches. By restricting user access based on roles and permissions, utilizing strong authentication methods, monitoring network activity, and limiting physical access to critical components, organizations can significantly enhance their network security posture.
Remember, effective network hardening involves a multi-layered approach that combines various security controls and practices to ensure comprehensive protection against evolving threats.
RELATED: Guarding Entry: Importance of Physical Access Control
Optimizing Server and Database Hardening
To ensure the security of your network, its crucial to optimize server and database hardening. By implementing proper access controls and regularly monitoring server performance, you can protect sensitive data from potential threats. Lets explore some key practices for optimizing server and database hardening.
Secure Server Configurations by Disabling Unnecessary Services
One essential step in network hardening is securing server configurations by disabling unnecessary services. This involves identifying any software or functionality that is not required for the servers operation and disabling or removing them. By doing so, you reduce the attack surface and minimize potential vulnerabilities.
Here are some pros of securing server configurations:
Enhanced Security: Disabling unnecessary services reduces the risk of exploitation by attackers.
Improved Performance: With fewer services running, system resources are freed up, resulting in better overall performance.
On the other hand, there may be a few cons to consider:
Limited Functionality: Disabling certain services may restrict some functionalities that could be useful for specific purposes.
Compatibility Issues: Removing certain services might lead to compatibility issues with other programs or applications.
Harden Databases by Implementing Proper Access Controls
Another critical aspect of network hardening is database hardening. It involves implementing proper access controls to safeguard sensitive data stored in databases. By carefully managing user permissions and roles, you can prevent unauthorized access to valuable information.
Consider these pros when implementing proper access controls:
Data Protection: Access controls ensure that only authorized individuals can view or modify sensitive data.
Compliance Requirements: Many industries have regulatory requirements regarding data protection. Implementing access controls helps meet these obligations.
However, there are a few cons worth noting:
Administrative Overhead: Managing user permissions and roles requires ongoing administrative efforts.
Potential User Restrictions: Strict access controls may limit certain users ability to perform their tasks efficiently if not properly configured.
Regularly Backup Server Data to Prevent Loss in Case of an Attack
Backing up server data is a crucial practice for network hardening. Regular backups help protect against data loss and enable quick recovery in case of an attack or system failure.
Consider these pros when regularly backing up server data:
Data Recovery: Backups ensure that even if your server is compromised, you can restore the system and recover critical data.
Business Continuity: In the event of a cyberattack or hardware failure, regular backups minimize downtime and ensure business continuity.
However, there are a few cons to keep in mind:
Storage Requirements: Regular backups consume storage space, so its essential to allocate sufficient resources for this purpose.
Backup Frequency: Determining the appropriate backup frequency depends on factors such as the volume of data changes and acceptable downtime.
RELATED: Understanding Backup Methods: Full vs Incremental vs Differential Backup
Monitor Server Performance for Any Signs of Compromise
Monitoring server performance is a vital step in network hardening. By observing key metrics and indicators, you can detect any signs of compromise or unusual activity promptly.
Here are some pros associated with monitoring server performance:
Early Detection: Monitoring allows you to identify potential security breaches early on and take immediate action.
Performance Optimization: Monitoring helps identify bottlenecks or issues affecting server performance, allowing for timely resolutions.
RELATED: The Importance of Monitoring your Application Performance
Securing Network Components and Port Management
To ensure the security of your network infrastructure, it is crucial to implement effective network hardening practices. This involves securing network components and managing ports to minimize vulnerabilities and protect against potential cyber threats. Here are some key steps you can take:
Close unused ports to reduce the attack surface area
One important aspect of network hardening is closing any unused ports on your network devices. Open ports provide potential entry points for attackers, so its essential to identify and close those that are not necessary for business services or application communications.
By reducing the number of open ports, you can significantly decrease the attack surface area and limit potential avenues for unauthorized access.
Segment the network into separate zones with different security levels
Another critical step in securing your network infrastructure is segmenting it into separate zones with varying security levels. This segmentation helps isolate sensitive data or critical systems from less secure areas, providing an additional layer of protection against unauthorized access or lateral movement by attackers.
Regularly update firmware on routers, switches, and other devices
Keeping your network devices up to date with the latest firmware is vital for maintaining their security posture. Firmware updates often include patches for known vulnerabilities or weaknesses that could be exploited by attackers. By regularly updating firmware on routers, switches, and other devices, you can ensure that they have the latest security enhancements.
Monitor network traffic for suspicious activities or anomalies
Implementing robust monitoring capabilities allows you to detect any suspicious activities or anomalies within your network traffic. By analyzing network logs and employing intrusion detection systems, you can identify potential threats in real-time and respond promptly to mitigate any risks.
By following these network hardening practices, you can significantly enhance the security of your network infrastructure. Remember to regularly review and update password configurations, maintain secure firewall rules, and ensure proper configuration of all network devices.
Conducting periodic security audits and penetration testing can help identify any weaknesses or vulnerabilities that need to be addressed promptly.
Remember, securing your network is an ongoing process that requires continuous attention and updates. Stay vigilant and proactive in implementing these measures to protect your businesss critical assets from cyber threats.
Importance of Network Hardening
In todays digital landscape, network hardening plays a crucial role in safeguarding sensitive information and protecting against cyber threats. By implementing robust security measures, organizations can significantly reduce the risk of unauthorized access, data breaches, and other malicious activities. Network hardening involves strengthening the security posture of a network infrastructure by employing various techniques and best practices.
To ensure the utmost protection, it is essential to understand systems hardening and explore different network security techniques. By optimizing server and database hardening, organizations can fortify their networks against potential vulnerabilities. Implementing access controls for networks and securing network components and port management are vital steps in building a resilient defense system.
To enhance your organizations network security, consider implementing the best practices for network hardening outlined in this blog post. By following these guidelines, you can mitigate risks effectively and protect your valuable assets from potential threats. Remember that network hardening is an ongoing process that requires regular updates and maintenance to adapt to evolving cybersecurity landscapes.
Network Hardening: Frequently Asked Questions
What are some common network vulnerabilities?
Network vulnerabilities can arise from various factors such as outdated software or hardware, weak passwords, misconfigured firewalls or routers, lack of encryption protocols, unpatched systems or applications, social engineering attacks, etc.
How does network hardening protect against cyber threats?
Network hardening strengthens the security posture of a network infrastructure by implementing various security measures such as access controls, encryption protocols, regular patching and updates, intrusion detection systems (IDS), firewalls with strict rule sets, strong authentication mechanisms like multi-factor authentication (MFA), etc., which collectively help protect against cyber threats.
Are there any specific tools or software recommended for network hardening?
There are several tools available that can aid in the process of network hardening such as vulnerability scanners like Nessus or OpenVAS for identifying weaknesses in your system; firewall management tools like Cisco ASA for configuring and monitoring firewalls; network monitoring tools like Wireshark or Nagios for detecting suspicious activities; and intrusion detection/prevention systems (IDS/IPS) like Snort or Suricata for real-time threat detection.
How often should network hardening measures be updated?
Network hardening measures should be regularly reviewed, updated, and tested to ensure they are effective against the latest threats. It is recommended to conduct periodic security assessments, vulnerability scans, and penetration tests to identify any weaknesses in your network infrastructure.
What role does employee training play in network hardening?
Employee training plays a crucial role in network hardening as human error is often exploited by cybercriminals. By educating employees about best practices such as strong password management, recognizing phishing attempts, practicing safe browsing habits, and reporting suspicious activities promptly, organizations can significantly reduce the risk of successful attacks on their networks.