Securing Your Smart Home Essential Tips for Protecting Connected Devices
Tips for Securing Your Devices
Tips for Securing Your Devices
You use your devices to store and process sensitive information every day, which makes securing your devices an important part of securing both your identity and your data. It also makes your system more stable, which leads to better performance and less time troubleshooting problems.
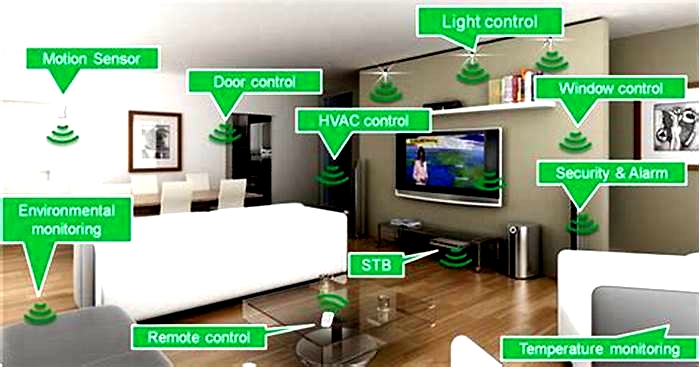
The Internet of Things (IoT) continues to expand as more of our things become connected. The IoT can include watches, televisions, appliances, smart speakers, security systems, vehicles, and much more. Networked smart homes are common.
Make sure all connected devices have security precautions. Understand what information your devices collect and how that information is managed and used. To ensure that a new device is an asset, rather than a liability, here are a few things to keep in mind:
Encrypt your devices.
Encryption ensures that data on a lost or stolen device cannot be accessed by an unauthorized individual. Most desktops, laptops, tablets, and smartphones can be encrypted.
Configure automatic updates for operating systems and applications.
Software companies regularly release updates to improve the performance and security of their applications. Run updates automatically, where possible, on all of your devices, and restart your devices in a timely manner when prompted to complete the updates.
Install antivirus software.
Northwestern recommends downloadingantivirus softwareto all students, faculty, and staff. Many antivirus apps are available through app stores on tablets and smartphones.
Install ad-blocking software and adjust your browser security settings.
Secure your browser to prevent malicious software from being accidentally downloaded. Hackers sometimes insert malware into ads that run automatically on page load or create pop-ups that pretend to be your antivirus software or other applications on your system waiting for updates.
Use PINs/passwords/fingerprints/face recognition to access devices.
Use PINs, passwords, and fingerprints to access devices, enable remote-wipe features, and configure automatic screen timeouts. Some devices also have face recognition technology. This information is especially true for portable devices, which are easily lost or stolen.
Smartphones and tablets are frequently logged into multiple accounts, such as email and social media, that could provide unauthorized individuals with access to personal information.
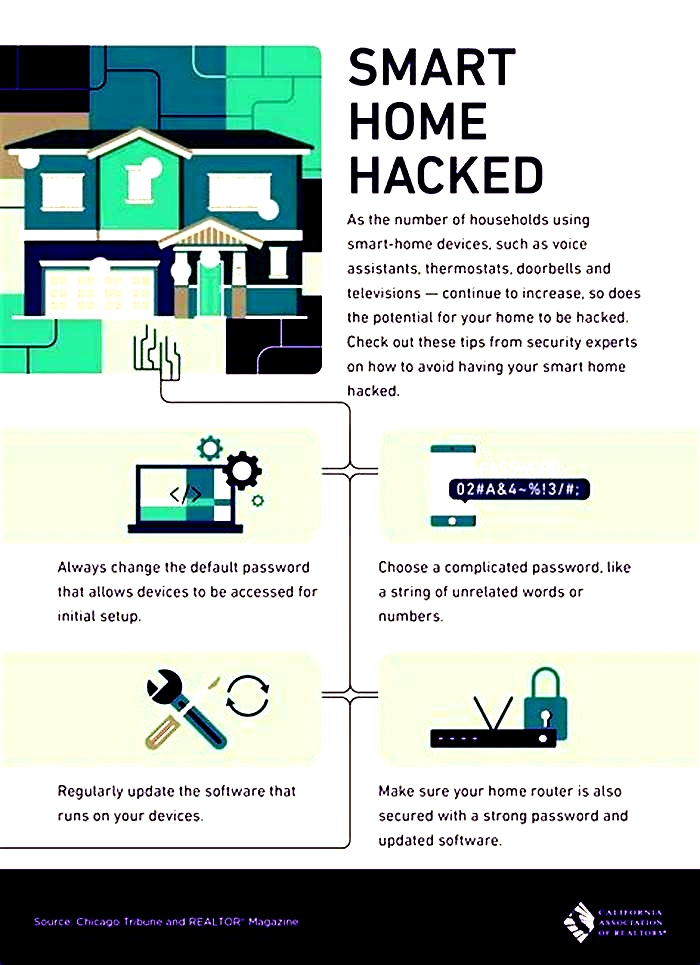
Change default passwords on networked devices.
Networked devices, such as routers and printers, frequently come with special interfaces that are intended to provide easy configuration but do not force you to change the default password during setup. This situation may make your device accessible on the internet at a predictable address using a predictable password and can allow hackers to capture traffic or attack other devices on your network.
Disable unnecessary services on networked devices, such as routers and printers.
FTP, Telnet, and other services can provide vulnerabilities for hackers to attack, especially if the device is not updated frequently. Disable services you are not using to reduce the number of windows into your system.
Do not open unexpected links or attachments in emails.
Phishing emails commonly attempt to entice or alarm you to get you to install malware accidentallyfake invoices and shipping notifications are especially common, particularly around the holiday season. Word document attachments may prompt you to enable macros to view them. If you were not expecting to receive an attachment, contact the sender directly to verify its credibility. How to recognize a phishing attempt.
Be careful about what you visit on the web.
Web pages automatically load text and multimedia content when you visit them, and some of this content can be malicious.
The more you stray away from widely publicized, well-known sites, the riskier visiting the sites can be. Long, complex URLs are frequently a sign that you are off the beaten path.
Be careful what you download.
Only install reviewed applications from reputable sources. Do not download updates or applications while on networks that are shared with strangers (e.g., airports, cafes, hotels, etc.) unless you are using a VPN. Other individuals on the network may be able to masquerade as an access point and send malware to your device in place of updates.
Do not engage in illegal file-sharing.
Peer-to-peer file sharing usually involves downloading unknown content from unknown devices and trusting that the content is what it claims to be.
Accidentally torrenting malware is especially likely when you cannot find content from a reputable source, as is the case with illegally distributed copyrighted materials.
How to Secure Your IoT Devices: Best Practices of IoT Home Security
Its more crucial now than ever to implement IoT security best practices. Heres why. There was an increase in cyberattacks at the beginning of 2023.
A staggering 54% of companies experienced an average of over 60 attacks every week! These attacks targeted IoT devices like routers, IP cameras, DVRs, and more.
This was more than three times the number from the previous two years and represented a 41% rise from the prior year.
Of course, this doesnt mean individuals are excluded from these cyber attacks. For example, there was a 77% increase in malware attacks on IoT devices in the first half of 2022.
IoT devices are becoming more common in remote work and study environments, making them attractive targets for cybercriminals.
This article will discuss how to secure IoT devices properly to protect themyour IoT devices from this emerging threat.
Lets begin.
Common IoT Security Threats
Before we show you how to protect IoT devices from hackers, here are some of the common IoT security threats you should know:
1. Botnet Attacks
Because Internet of Things devices lack the robust security measures of more advanced computers, they are vulnerable to malware attacks.
A single IoT device infected by an attacker doesnt cause much damage. However, if they take over many IoT devices, they can build a botnet.
It resembles an army of compromised devices that collaborate to attack other networked systems.
Attackers can direct these infected devices to tasks like overwhelming a network with data or sending spam using a botnet.
The Mirai Botnet Attack
The Mirai botnet attack occurred in 2017, where cybercriminals used a massive IoT botnet to interfere with Dyn, a DNS service provider. Huge portions of the Internet were down due to this one attack.
This affected well-known media outlets like Reddit, Netflix, Twitter, and CNN. The malware that infected the IoT devices gave rise to the botnets name, Mirai.
Many of these devices had weak passwords and outdated software, making it easy for hackers to get access and take over.
2. Man-in-the-Middle (MITM) Attacks
Cybercriminals can take advantage of gaps in IoT devices network communication protocols. They can get private, sensitive data this way.
They might even change the information transferred between IoT devices and servers to gain access to private data or the system.
3. Ransomware
Even though most IoT devices dont hold sensitive information, ransomware can still affect them. IoT device ransomware attacks typically dont encrypt data for a ransom.
Instead, they turn off the devices primary features. This may include turning off a camera or microphone or shutting down an essential industrial device for the company.
For example, the Colonial Pipeline attack caused the corporation to cease operations to stop ransomware from causing significant harm.
This caused fuel shortages in the US Southeast. The results might have been disastrous if the malware had spread further.
4. Privilege Escalation
Cybercriminals can get unwanted access to a network by taking advantage of bugs, unresolved issues, or design faults in IoT devices.
After theyre inside, they can take advantage of other problems to access higher levels. This can cause the system to be controlled.
5. DDoS
DDoS attacks have significantly increased over the years. This increase may be related to botnets and compromised IoT devices.
When botnet malware infects IoT devices, cybercriminals can use those devices as tools for massive cyberattacks like DDoS attacks.
Related: TOP 10 Cyber Security Threats: All You Need to Know
In the following sections, well show you how to secure your smart home devices.
How to Secure IoT Devices: IoT Best Practices
Here are the IoT security best practices to help you secure your IoT devices:
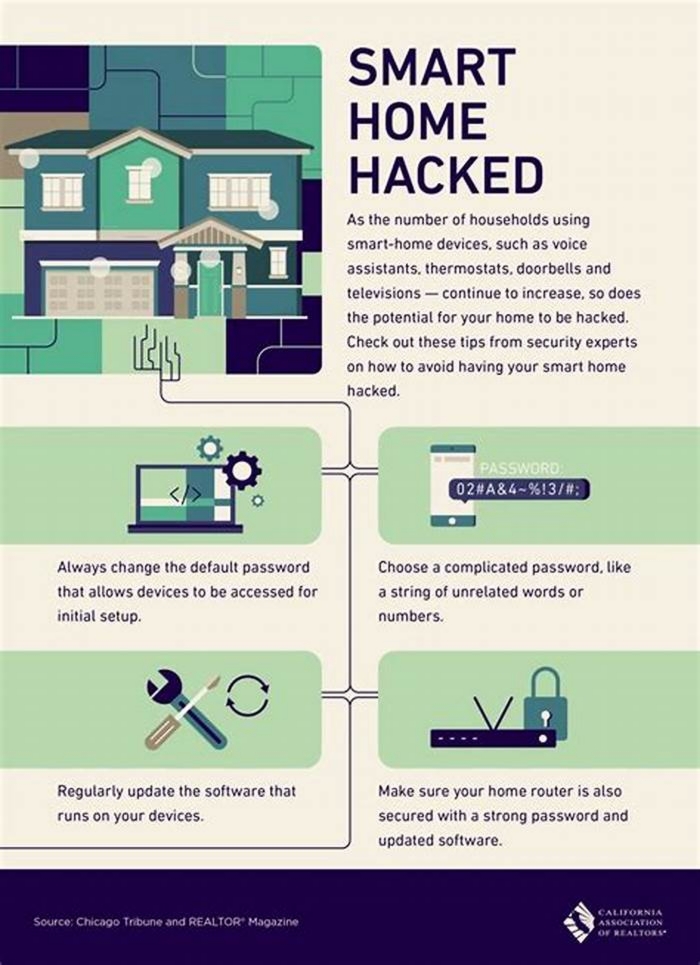
1. Set Your Router Properly
Correct Wi-Fi router setup is one of the crucial factors in securing IoT devices for a safe, smart home. Since your router is the main entry point for all your IoT devices, hackers will attack it heavily.
Since the manufacturers default name usually contains easily accessible information, change the routers name.
Choose a unique name that conceals personal information. Also, create a unique, powerful password by combining letters, numbers, and symbols.
Create an unbreakable password with a random password generator for extra security. Also, confirm that your router uses the strongest encryption, such as WPA2 (the most recent standard is WPA3).
It could be time to upgrade your router if it only supports outdated protocols like WPA or WEP.
Related: Stay Safe Online: The Best Ways to Store Passwords
2. Disable Features You Dont Use
IoT devices frequently have remote control features, even those we use primarily for residential Wi-Fi networks. Its advisable to turn off remote access in these situations.
Also, some smart devices might not need Bluetooth. An example is speakers with Wi-Fi and Bluetooth. Turn off any features you arent using.
Voice control is a feature that many smart TVs have, but its usually ignored even in homes with voice-activated assistants like Google Assistant, Siri, or Alexa.
As a security precaution, turning off these rarely used features can help prevent your chats from being hacked by a compromised microphone.
This can reduce possible entry points and improve security in general. These are some ways of securing IoT devices at home.
Related: How to Stop Voice Assistants From Listening to Your Voice?
3. Enable Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds a degree of security to password-only security, typically in the form of two-factor authentication (2FA).
You need further identity verification when someone tries to access your Internet of Things devices in your home.
A one-time pin (OTP) or verification code given to your phone or email to verify the persons identity can serve as this proof.
Although most smart devices already have 2FA enabled, you can use third-party apps like Google Authenticator to enable it for those that dont.
Adding a layer of security through a reliable third-party provider can give you additional peace of mind, even if your IoT device already offers 2FA through its mobile app.
So, if you want to know how to protect IoT devices, consider two-factor authentication.
Related: How to Turn Off Two-Factor Authentication?
4. Perform Penetration Testing
One way to know how to manage IoT devices is to conduct penetration testing. Connected devices usually have built-in vulnerabilities because they are meant to be user-friendly.
Before integrating IoT devices into your home, perform in-depth evaluations or penetration tests on the related hardware, software, and equipment.
Penetration testing evaluates security policies, regulatory compliance, risk response, and finding and understanding vulnerabilities.
You can take proactive steps to protect yourself from future IoT threats by doing a penetration test before using IoT devices.
Its one of the Internet of Things home security measures you can implement.
Also Read: Ultimate Guide to Online Safety: How to Prevent Phishing Attacks
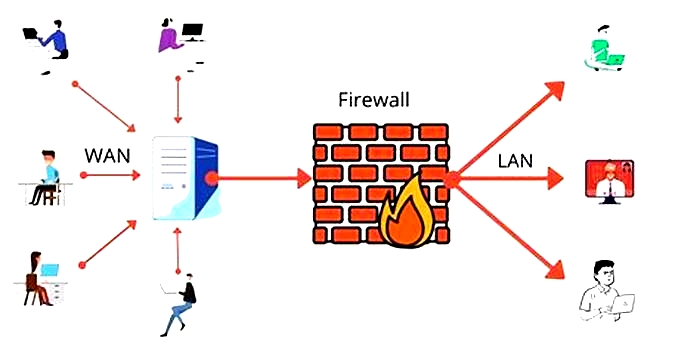
5. Improve Your Security Through Network Segmentation
If you want to know how to secure IoT devices on a home network, use network segmentation. Whenever you integrate IoT devices into your network, you should always consider that there could be security breaches.
You can then be proactive and prepared to act if a breach occurs. Network segmentation divides your computer network into smaller sub-networks.
Its one of the best ways of securing IoT devices. With this strategy, your company can stop unauthorized users from infiltrating neighboring subnetworks.
Also, network segmentation strengthens your overall security by reducing the number of possible entry points to critical data within the segmented areas.
6. Keep Your Software Updated
Its crucial to install any software updates that come in for your phone. Usually, these updates come with fixes to address security flaws.
Updating your system software is essential for safeguarding your devices against online dangers. If you want to know how to control IoT devices, update your software.
Tips for Securing Specific IoT Devices
If you want to know how to control IoT devices, follow the tips to secure your specific IoT devices. Its crucial to protect your privacy and preserve the integrity of your connected home.
Here are some hints to secure specific IoT devices:
1. Smartphones and Tablets
Start with basic security measures like password-protected devices, device locks with PINs, or biometric locks. Update the operating system and apps frequently, and check and limit app permissions.
If your device is lost or stolen, you can secure your data by activating remote tracking.
2. Smart Speakers
To restrict device access to authorized users, consider changing the default wake word on smart speakers and turning on voice recognition.
Use secure Wi-Fi passwords and turn off the microphone when not in use. Remember to upgrade the firmware regularly to fix security vulnerabilities.
3. Smart Thermostats
You can secure your smart thermostats by changing the default login information, connecting smart thermostats to different networks, and ensuring encrypted data transmission.
If available, change the users rights and turn on two-factor authentication.
4. Smart Cameras
Smart cameras require strong, one-of-a-kind passwords in addition to regular software updates. To prevent unwanted catches, use secure Wi-Fi encryption, create privacy zones, and install cameras strategically to preserve your privacy.
IoT Security and Childrens Safety
As everyday objects become digitally connected in the IoT era, ensuring childrens safety has become more complex and challenging.
IoT technology brings a host of advances and conveniences. But it also poses security dangers that could affect children.
For example, smart toys are becoming more and more common in homes. Although these interactive devices can be educational and enjoyable, there are worries about their internet connectivity.
Cybercriminals can hack these devices without strong security measures and expose kids to unsuitable content or privacy violations.
This is exactly what happened to the Safe-KID-One smartwatch.
The Safe-KID-One Security Breach
The European Commission recalled the Safe-KID-One smartwatch due to serious privacy and security issues.
This watch, which had GPS tracking and calling capabilities, was sold as a kid safety tool. However, the Commission found serious security flaws.
For example, the mobile apps server communicates with the watch without encryption. This allowed unauthorized users to access personal information like phone numbers and location history.
This brought up possible risks to the safety of kids.
Take an Active Role in IoT Best Practices
Parents need to get involved in selecting and researching IoT toys with robust security measures.
Teaching kids the value of not disclosing personal information on these devices is also very important.
You can use these technologies while reducing threats to kids by understanding and addressing IoT security for childrens safety.
Conclusion
If you want to know how to secure IoT devices, follow the effective ways discussed in this guide. These IoT devices can make it more convenient to perform everyday activities.
However, as more and more IoT devices gain access to your house, the security of your data becomes a significant concern. Thats why its crucial to implement IoT security best practices to solve this issue.
Consider hiring IoT app developers, say using a hiring software, to build a robust security system for your house or business to safeguard your digital assets.
FAQ
How Often Should I Update My IoT Devices?
We recommend updating your IoT devices regularly to maintain their security and best performance. You should generally check for updates once a month. However, the frequency of updates can vary based on the manufacturer and the particular device.
How Can You Control an IoT-connected Smart Device?
An IoT-connected smart device is usually easy to control. You can control most devices using specific mobile apps the manufacturer offers. After installing it, you must connect your device to the app using your Wi-Fi network.
After pairing, you can use the app to operate your device by changing settings and monitoring its condition. You can use voice commands with services like Google Assistant or Alexa.
What Should I Do If My IoT Device Is Compromised?
You must act quickly to protect your security and privacy if you believe your IoT device has been compromised. First, unplug the compromised device from the power supply and your network. For your network and the device, change the access information and passwords.
To fix any vulnerabilities, update the firmware and software on the device to the most recent version. If you need further help protecting your device, contact a cybersecurity expert or the device manufacturers customer service team.
There are several IoT home security tools you can use for free. First, ensure your Wi-Fi network and every device have strong, unique passwords. Also, use network segmentation to separate IoT devices from your critical systems.
Free smartphone apps with integrated security measures are available from certain manufacturers. To monitor and secure IoT devices on your network, you can also investigate open-source security solutions like Home Assistant.