Penetration Testing Your Network Security Identifying Vulnerabilities Before Hackers Do
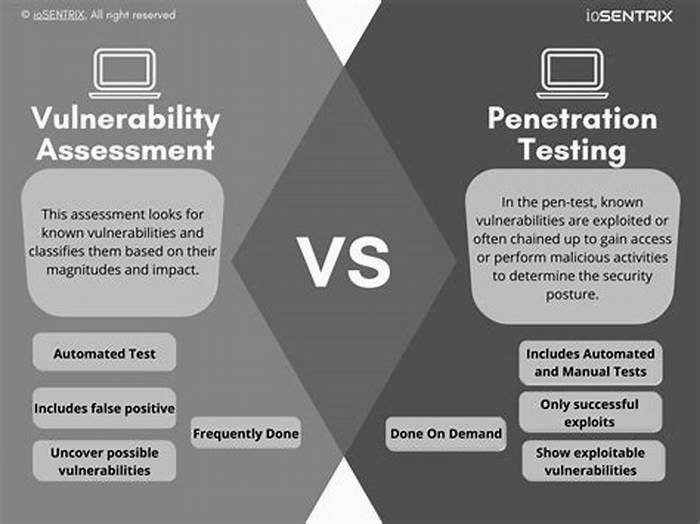
Penetration testing explained: How ethical hackers simulate attacks
- An external penetration test simulates what you might imagine as a typical hacker scenario, with an outsider probing into the target organizations perimeter defenses to try to find weaknesses to exploit.
- An internal test, by contrast, shows what an attacker whos already inside the networka disgruntled employee, a contractor with nefarious intentions, or a superstar hacker who gets past the perimeterwould be capable of doing.
- A blind test simulates a real attack from the attackers end. The pen tester is not given any information about the organizations network or systems, forcing them to rely on information that is either publicly available or that they can glean with their own skills.
- A double-blind test also simulates a real attack at the target organizations end, but in this type of engagement the fact that a penetration test is being conducted is kept secret from IT and security staff to ensure that the companys typical security posture is tested.
- A targeted test, sometimes called a lights-turned-on test, involves both the pen testers and the targets IT playing out a simulated war game in a specific scenario focusing on a specific aspect of the network infrastructure. A targeted test generally requires less time or effort than the other options but doesnt provide as complete a picture.
App security firm Synopsis lays out another way to think about varying test types, based on how much preliminary knowledge about the target organization the testers have before beginning their work. In a black box test, the ethical hacking team wont know anything about their targets, with the relative ease or difficulty in learning more about the target orgs systems being one of the things tested. In a white box test, the pen testers will have access to all sorts of system artifacts, including source code, binaries, containers, and sometimes even the servers running the system; the goal is to determine how hardened the target systems are in the face of a truly knowledgeable insider looking to escalate their permissions to get at valuable data. Of course, a real-world attackers preliminary knowledge might lie somewhere between these two poles, and so you might also conduct a gray box test that reflects that scenario.
Penetration testing steps
While each of these different kinds of penetration tests will have unique aspects, the Penetration Test Executing Standard (PTES), developed by a group of industry experts, lays out seven broad steps will be part of most pen testing scenarios:
- Pre-engagement interactions: As weve noted, any pen test should be preceded by the testers and target organization establishing the scope and goals of the test, preferably in writing.
- Intelligence gathering: The tester should begin by performing reconnaissance against a target to gather as much information as possible, a process that may include gathering so-called open source intelligence, or publicly available information, about the target organization.
- Threat modeling: In this phase, the pen tester should model the capabilities and motivations behind a potential real attacker, and try to determine what targets within the target organization might attract that attackers attention.
- Vulnerability analysis: This is probably the core of what most people think about when it comes to penetration testing: analyzing the target organizations infrastructure for security flaws that will allow a hack.
- Exploitation: In this phase, the pen tester uses the vulnerabilities theyve discovered to enter the target organizations systems and exfiltrate data. The goal here is not just to breach their perimeter, but to bypass active countermeasures and remain undetected for as long as possible.
- Post exploitation: In this phase, the pen tester attempts to maintain control of the systems theyve breached and ascertain their value. This can be a particularly delicate phase in regard to the relationship between the pen testers and their clients; it is important here that the pre-engagement interactions in the first phase produced a well-defined set of ground rules that will protect the client and ensure that no essential client services are negatively affected by the test.
- Reporting: Finally, the tester must be able to deliver a comprehensive and informative report to their client about the risks and vulnerabilities they discovered. CSO spoke to a number of security pros about the traits and skills an ethical hacker should have, and many of them said that the communication skills necessary to clearly convey this information is close to the top of the list.
The penetration testers suite of tools is pretty much identical to what a malicious hacker would use. Probably the most important tool in their box will be Kali Linux, an operating system specifically optimized for use in penetration testing. Kali (which most pen testers are more likely to deploy in a virtual machine rather than natively on their own hardware) comes equipped with a whole suite of useful programs, including:
ETHICAL HACKING
What is Ethical Hacking?
Malicious hackers use an array of tools and methodologies to breach cybersecurity, such as social engineering techniques or exploiting vulnerabilities in networks, configurations, and software withcross-site scripting (XSS),SQL injection (SQLI), and other types of attacks. Adding hurdles in their way are ethical hackers, also known as white hat hackers. Such professionals use their own sets of tools and assessment techniques to identify security vulnerabilities before malicious hackers can take advantage of them.
Read this in-depth guide for more on:
- What is ethical hacking?
- Is ethical hacking legal?
- White hat hacker vs black hat hacker vs gray hat hacker
- How to get into ethical hacking
Ethical hacking definition and meaning
Here is an ethical hacking definition in simple terms: ethical hacking is a legal and sanctioned attempt to circumvent thecybersecurity of a systemor application, typically to find vulnerabilities. Many ethical hackers try to operate from the mindset of a malicious hacker, using the same software and tactics.
An example of ethicalhackingis when a person is authorized by an organization to try and hack their web application. Another example is when a white hathackeris hired by an organization to test its staff with simulated social engineering attacks like phishing emails.
The importance of ethical hacking
- Tools and methodologies:The lessons learned from ethical hacking help with the creation of effective testing tools and methodologies. Such tools and methodologies further improve an organizations cybersecurity posture.
- Vulnerability identification:White hat hackers can find critical security flaws in systems, applications, and websites. Patching vulnerabilities before a malicious hacker can exploit them can enhance different types of security, includingInternet security. Vulnerability identification is also an important component ofvulnerability management.
- Incident Response:Ethical hackers can run attack simulations using the same methods and tools as malicious hackers to help security teams prepare for cyber threats. With the aid of cyber attack exercises, security teams can improve theirincident response planand reduce their incident response time.
- Anti-phishing:Many modern ethical hacking teams offer anti-phishing training services. Here, they use emails, text messages, phone calls, and baiting to test the readiness of organizations against threats that utilize phishing. Read about thishacking prankfor an example of a clever social engineering attack.
- Secure development:Some software developers hire ethical hackers to test their products during the development cycle. By ironing out vulnerabilities, developers can stop hackers from taking advantage ofzero-day bugs.
- Data security:Modern organizations manage different types of sensitive data. Malicious hackers can access this data by using social engineering attacks or exploiting software vulnerabilities. Ethical hackers can improve data security by running penetration testing and simulating phishing attacks.
- National security:National organizations such as security agencies and public sector organizations face sophisticated threats from state-sponsored entities. They can mitigate the risk of terror threats and cyber attacks by using the lessons learned from ethical hacking to improve their cybersecurity.
- Financial rewards:Some ethical hackers rely on contracts and programs to generate income. They can find full-time or part-time employment with companies that develop software or need to reduce security vulnerabilities. They can also earn rewards by finding security vulnerabilities in bug bounty programs.
- Financial losses:Companies can suffer significant financial losses due to the exploitation of software vulnerabilities by hackers. Ethical hackers can reduce the risk of long-term losses by improving security.
- Regulatory compliance: Organizations must comply with regulations concerning privacy and security. They can comply with such regulations more easily by hiring white hat hackers to find bugs that can be exploited by attackers.
- Reputational Damage:A cybersecurity attack can dent a companys reputation if it results in the loss of sensitive information. Running attack simulations and patching exploitable bugs with the assistance of ethical hacking can prevent incidents that damage an organizations standing with its clients and partners.
Who is an ethical hacker?
An ethical hacker is any person who attempts to circumvent the security of an organization, website, application, or network with legal consent. The goal of an ethical hacker is to locate weaknesses and vulnerabilities legally to help organizations mitigate the risk of exploits, breaches, social engineering campaigns and other kinds of cyberattacks. Professional ethical hackers work closely with security teams and offer detailed reports and proposals.
Understanding the different types of hackers
Although the term hacking is usually associated with negative connotations, there are several different types of hackers, includingwhite hat, back hat and gray hat hackers. Although all hackers attempt to find vulnerabilities, their motivations can vary.
White hat hackers
As mentioned, white hat hackers are also known as ethical hackers. They have consent from owners of systems to find security flaws through hacking, penetration testing, and anti-phishing simulation. White hat hackers can also use the same methods as malicious hackers to simulate attacks.
Black hat hackers
Black hat hackers are also known as malicious hackers. They break into systems and networks illegally. Black hat hackers engage in hacking to steal sensitive information like passwords, addresses, and credit card information, damage systems, or for spying.
Grey hat hackers
While gray hat hackers dont have malicious intentions, they operate outside the law. For example, they may break into a system without the consent of the system owner. Grey hat hackers may look for vulnerabilities to highlight them. Some gray hat hackers breach systems to show off, however, they dont steal data, nor do they cause any harm.
How does ethical hacking work: The 5 phases of ethical hacking
Reconnaissance: Gather information and plan approach
Ethical hackers usually start by defining the scope of their tasks in the first phase of ethical hacking. The planning phase depends on the project, tools, methodologies, and objectives outlined by the organization and security partners. The ethical hacker may also utilize search engines and other tools to gather information about the target.
Scanning: Scan for vulnerabilities
After gathering information and planning the approach, an ethical hacker usually scans the target for vulnerabilities. The goal is to find entry points and flaws that can be exploited most easily. Ethical hackers may use scanning tools like port scanners, dialers, network scanners, web app scanners, etc.
Gaining access: Break into the system
With the vulnerability assessment complete, the ethical hacker begins to take advantage of the security flaws. Ethical hackers can use different tools and methods, including technology utilized by malicious hackers. However, they avoid tools and areas outside of the scope defined by their client.
Maintaining access: Retain your access
After breaching the targets security, an ethical hacker thinks like a malicious hacker by trying to maintain access for as long as possible and evading security measures. They also gain an understanding of the potential damage they can cause, such as data theft, privilege escalation, malware drops, lateral movements, opening backdoors and more.
Post-attack: Documentation, remediation, and follow-up [H3]
After exploitation, the ethical hacker offers a detailed report of their actions. The report includes details of the breach, identified security flaws, and suggestions for remediation. Their client may follow recommendations from the report to apply patches, reconfigure or even reinstall systems, change access controls, or invest in new security tools. The ethical hacker may simulate a second attack to check the effectiveness of the remedial measures.
The difference between ethical hacking and penetration testing
Many experts classify penetration testing as a subset of ethical hacking. While ethical hacking is a general term for finding cybersecurity vulnerabilities in a system with the consent of its owner, penetration is a specific technique that utilizes a systemic approach involving targeting, analysis, exploitation, and remediation.
Organizations hire penetration testers to improve their cybersecurity posture. Penetration testers are authorized to simulate attacks on a computer system and may use the same tools and methodologies as black hat hackers to demonstrate the flaws in a system. Some penetration testers are given instructions ahead of the attack while others are given no information and are required to gather intelligence on their own. In covert penetration tests, the cybersecurity team of an organization is kept completely in the dark about the simulated attack to make the test more authentic.
Ethical hacker responsibilities
Authorization
The first responsibility of an ethical hacker is to have authorization for hacking. In other words, they must have consent from their target before hacking their systems. Its also a good idea to have the scope of the test defined and written beforehand to prevent any legal problems.
Confidentiality
After beginning the task, they must avoid any activity that may harm their client or is out of the agreed-upon boundaries of the ethical hacking project. Ethical hackers should also remain professional and respect the privacy of everyone involved. Some ethical hackers must sign non-disclosure agreements for the protection of their clients.
Penetration testing
As mentioned, penetration testing is a type of ethical hacking. White hat hackers use penetration testing to find and exploit vulnerabilities in a computer system. The goal is to test the defences of a system, offer recommendations, and show how easily a threat actor can initiate an effective cyberattack.
Testing authentication
Authentication is the process of verifying the identity of the user of a system. Threat actors try to breach theauthenticationprocess to gain unauthorized access to confidential data or complete other malicious tasks. Ethical hackers can help test the strength of an authentication system by testing passwords, lockout mechanisms, and the account recovery process by simulating brute force attacks, multi-factorfatigue attacks, and more.
Social engineering attacks
Ethical hackers can simulate attacks like spearing-phishing, smishing, vishing, pretexting, and baiting, to test an organizations readiness against social engineering attacks. An ethical hacker may also deploy scareware, which is malicious software that uses fictitious threats and false alarms to test how people react.
Identify weaknesses
Ethical hackers must use their skill set, training, techniques and tools to identify all weaknesses within the parameters of the simulated attack. Finding vulnerabilities is usually an ethical hackers primary task, and they must be thorough. The vulnerabilities can include zero-day flaws, misconfigurations, or other weaknesses.
Erasing hacks
Ethical hackers should remediate security loopholes to prevent malicious hackers from utilizing them. They should remove any traces of their activities, including malicious software. Folders, applications, and files should be restored to their original status.
Ethical hacking training
In addition to knowing common programming languages, ethical hackers should know about hardware, reverse engineering, and networking. They should also complete the right certifications and stay up to date in their field about threats and security vulnerabilities. They can tackle the latest security threats and utilize the newest remediation measures by upgrading their training and staying in touch with cybersecurity groups.
Reporting
A professional ethical hacker must offer a thorough report of their actions to their client. The report must include an account of discovered vulnerabilities and suggestions for improvement.
Ethical hacking vs. traditional hacking
A conventional hacker tries to gain unauthorized access to a system for personal gain or notoriety. In the process, they may damage their target, use malware like ransomware, or steal confidential information. However, an ethical hacker mimics the actions of a traditional malicious hackerwiththe authorization of their client. Instead of personal gain, ethical hackers use their knowledge and skills to harden the cybersecurity of an organization.
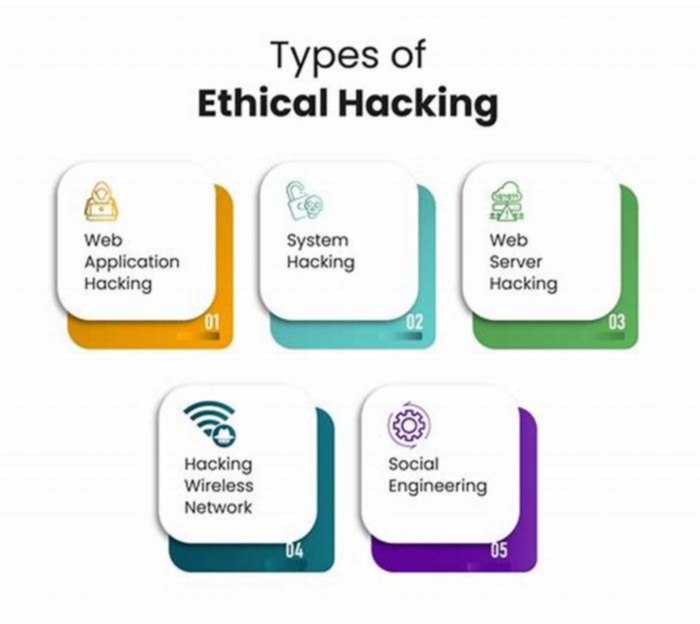
Ethical hacking examples: Types of ethical hacking
- System hacking involves the assessment of computer systems such as workstations.
- Network hacking tests technology like routers, switches, VPNs, and firewalls.
- Web server hacking assesses the security of web applications by simulating attacks like SQL injection and cross-site scripting (XSS).
- Wireless network hacking checks the strength of WiFi network security by testing passwords, encryption protocols, and access points.
- App hacking is the testing of applications on endpoints like smartphones, tablets, and laptops.
- Social engineering tests human resources by using psychology to breach cybersecurity.
Common vulnerabilities found by ethical hackers
- Flawed authentication measurescan be a dangerous attack vector.
- Misconfigured security protocolscan often be manipulated by malicious hackers to breach cybersecurity.
- Injection attacks allow threat actors to inject malicious code into data snippets and attackvulnerable web apps.
- Information exposure in an organization due toinadequate data securitycan result in a costlydata breach.
- Usingsoftware or hardware with known vulnerabilitiescan be a recipe for disaster.
Commonly used ethical hacking tools
Ethical hackers use a number of penetration testers, network scanners, and other security testing tools to find security vulnerabilities.
Nmap
Nmap, short for network mapper, is one of the most popular network scanning and mapping tools for security auditing. Ethical hackers can use their baked-in library to scan for open ports and find vulnerabilities in target systems. Nmap also works on some rooted and unrooted phones.
Wireshark
Wireshark is one of the most popular packet sniffers in the world. It grabs entire streams of traffic while listening to a network connection in real-time. Ethical hackers can analyze network traffic with this network protocol analyzer to find vulnerabilities and other issues.
Burp Suite
Burp Suite is a comprehensive web security testing platform. Ethical hackers can use it to scan, intercept and modify traffic, and scan for flaws in web applications. It includes a proxy server, repeater, and intruder mode. Burp Suite also has useful tools such as Spider, Intruder, and Repeater.
The future of ethical hacking
As cybersecurity threats grow more frequent and complex, expect the ethical hacking industry to expand further. More organizations are using ethical services to remediate vulnerabilities and protect themselves and their clients. Ethical hackers may use more complex tools and methodologies in the future that utilize artificial intelligence (AI) and machine learning (ML) for more effective attack simulations.