How to Protect Your Computer from Ransomware and Cyber Attacks Effectively Safeguarding Your Data and Privacy

Protect your PC from ransomware
Ransomware is malware that encrypts your filesor stops you from using your computer until you pay money (a ransom) for them to be unlocked. If your computer is connected to a network the ransomware may also spread to other computers or storage devices on the network.
Some of the ways you can get infected by ransomware include:
Visiting unsafe, suspicious, or fake websites.
Opening file attachments that you werent expecting orfrom people you dont know.
Opening malicious or bad links in emails, Facebook, Twitter, and other social media posts, or in instant messenger or SMS chats.
You can often recognize a fake email and webpage because they have bad spelling, or just look unusual. Look out for strange spellings of company names (like "PayePal" instead of "PayPal") or unusual spaces, symbols, or punctuation (like "iTunesCustomer Service" instead of "iTunes Customer Service").
Ransomware can target any PCwhether its a home computer, PCs on an enterprise network, or servers used by a government agency.
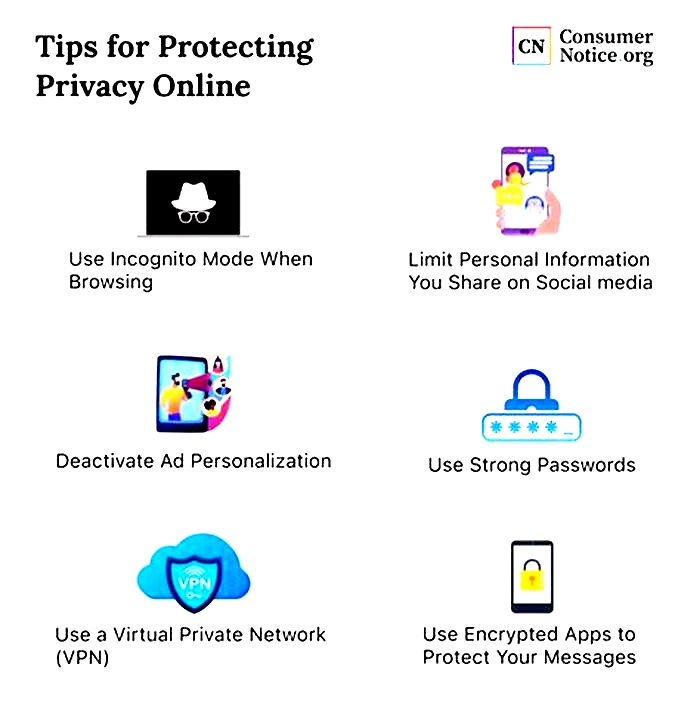
How can I help keep my PC secure?
Make sure your PC is up to date with the latest version of Windows and all the latest patches. Learn more about Windows Update.
Be sure Windows Securityis turned on to help protect you from viruses and malware (or Windows Defender Security Center in previous versions of Windows 10).
In Windows 10 or 11 turn on Controlled Folder Access to protect your important local folders from unauthorized programs like ransomware or other malware.
Get ransomware detection and recovery withMicrosoft 365 advanced protection.
Store important files on Microsoft OneDrive. OneDrive includes built in ransomware detection and recoveryas well as file versioning so you can restore a previous version of a file. And when you edit Microsoft Office files stored on OneDrive your work is automatically saved as you go.
Use a secure, modern, browser such as Microsoft Edge.
Restart your computer periodically; at least once a week. This can help ensure the applications and operating system are up-to-date and helps your system run better.
If you actually get a ransomware infection
Unfortunately, a ransomware infection usually doesnt show itself until you see some type of notification, either in a window, an app, or a full-screen message, demanding money to regain access to your PC or files. These messages often display after encrypting your files.
Try fully cleaning your PC with Windows Security. You should do this before you try to recover your files. Also see Back up your Windows PCfor help on backing up and recovering files for your version of Windows.
Don't pay money to recover your files. Even if you were to pay the ransom, there is no guarantee that you'll regain access to your PC or files.
What to do if you already paid
If youve already paid the ransom, immediately contact your bank and your local authorities. If you paid with a credit card, your bank may be able to block the transaction and return your money.
You can also contact the following government fraud and scam reporting websites:
If your region isn't listed here, Microsoft recommends that you contact your region's federal police or communications authority.
For an illustrated overview about ransomware and what you can do to help protect yourself, see The 5Ws and 1H of ransomware.
If you're in an enterprise,see theMicrosoft Malware Protection Centerfor in-depth information about ransomware.
Ransomware
All about ransomware attacks
Ransomware made headlines throughout 2021 and continues to make the news in 2022. You may have heard stories of attacks on large companies, organizations, or government agencies, or perhaps you as an individual have experienced a ransomware attack on your own device.
Its a significant problem and a scary prospect to have all of your files and data held hostage until you pay up. If you want to know more about this threat, read on to learn about ransomwares different forms, how you get it, where it comes from, who it targets, and ultimately, what you can do to protect against it.
What is ransomware?
Ransomware definition
Ransom malware, or ransomware, is a type of malware that prevents users from accessing their system or personal files and demands ransom payment in order to regain access. While some people might think a virus locked my computer, ransomware would typically be classified as a different form of malware than a virus.
The earliest variants of ransomware were developed in the late 1980s, and payment was to be sent via snail mail. Today, ransomware authors order that payment be sent via cryptocurrency or credit card, and attackers target individuals, businesses, and organizations of all kinds. Some ransomware authors sell the service to other cybercriminals, which is known as Ransomware-as-a-Service or RaaS.
Ransomware attacks
How exactly does a threat actor carry out a ransomware attack? First, they must gain access to a device or network. Having access enables them to utilize the malware needed to encrypt, or lock up, your device and data. There are several different ways that ransomware can infect your computer
How do I get ransomware?
- Malspam: To gain access, some threat actors use spam, where they send an email with a malicious attachment to as many people as possible, seeing who opens the attachment and takes the bait, so to speak. Malicious spam, or malspam, is unsolicited email that is used to deliver malware. The email might include booby-trapped attachments, such as PDFs or Word documents. It might also contain links to malicious websites.
- Malvertising: Another popular infection method is malvertising. Malvertising, or malicious advertising, is the use of online advertising to distribute malware with little to no user interaction required. While browsing the web, even legitimate sites, users can be directed to criminal servers without ever clicking on an ad. These servers catalog details about victim computers and their locations, and then select the malware best suited to deliver. Often, that malware is ransomware.Malvertising often uses an infected iframe, or invisible webpage element, to do its work. The iframe redirects to an exploit landing page, and malicious code attacks the system from the landing page viaexploit kit. All this happens without the users knowledge, which is why its often referred to as a drive-by-download.
- Spear phishing: A more targeted means to a ransomware attack is throughspear phishing. An example of spear phishing would be sending emails to employees of a certain company, claiming that the CEO is asking you to take an important employee survey, or the HR department is requiring you to download and read a new policy. The term whaling is used to describe such methods targeted toward high-level decision makers in an organization, such as the CEO or other executives.
- Social engineering: Malspam, malvertising, and spear phishing can, and often do, contain elements ofsocial engineering. Threat actors may usesocial engineering in order to trick people into opening attachments or clicking on links by appearing as legitimatewhether thats by seeming to be from a trusted institution or a friend. Cybercriminals use social engineering in other types of ransomware attacks, such as posing as the FBI in order to scare users into paying them a sum of money to unlock their files. Another example of social engineering would be if a threat actor gathers information from your public social media profiles about your interests, places you visit often, your job, etc., and using some of that information to send you a message that looks familiar to you, hoping youll click before you realize its not legitimate.

Encrypting files & demanding a ransom
Whichever method the threat actor uses, once they gain access and the ransomware software (typically activated by the victim clicking a link or opening an attachment) encrypts your files or data so you cant access them, youll then see a message demanding a ransom payment to restore what they took. Often the attacker will demand payment via cryptocurrency.
Types of ransomware
Three main types of ransomware include scareware, screen lockers, and encrypting ransomware:
- Scareware: Scareware, as it turns out, is not that scary. It includes rogue security software and tech support scams. You might receive a pop-up message claiming that malware was discovered and the only way to get rid of it is to pay up. If you do nothing, youll likely continue to be bombarded with pop-ups, but your files are essentially safe. A legitimate cybersecurity software program would not solicit customers in this way. If you dont already have this companys software on your computer, then they would not be monitoring you for ransomware infection. If you do have security software, you wouldnt need to pay to have the infection removedyouve already paid for the software to do that very job.
- Screen lockers: Upgrade to terror alert orange for these guys. When lock-screen ransomware gets on your computer, it means youre frozen out of your PC entirely. Upon starting up your computer, a full-size window will appear, often accompanied by an official-looking FBI or US Department of Justice seal saying illegal activity has been detected on your computer and you must pay a fine. However, the FBI would not freeze you out of your computer or demand payment for illegal activity. If they suspected you of piracy, child pornography, or other cybercrimes, they would go through the appropriate legal channels.
- Encrypting ransomware: This is the truly nasty stuff. These are the guys who snatch up your files and encrypt them, demanding payment in order to decrypt and redeliver. The reason why this type of ransomware is so dangerous is because once cybercriminals get ahold of your files, no security software or system restore can return them to you. Unless you pay the ransomfor the most part, theyre gone. And even if you do pay up, theres no guarantee the cybercriminals will give you those files back.
Mac ransomware

Not ones to be left out of the ransomware game, Mac malware authors dropped the first ransomware for Mac OSes in 2016. Called KeRanger, the ransomware infected an app called Transmission that, when launched, copied malicious files that remained running quietly in the background for three days until they detonated and encrypted files. Thankfully, Apples built-in anti-malware program XProtect released an update soon after the ransomware was discovered that would block it from infecting user systems. Nevertheless, Mac ransomware is no longer theoretical.
Following KeRanger were Findzip and MacRansom, both discovered in 2017.More recently in 2020, there was what looked like ransomware (ThiefQuest, aka EvilQuest), but it turned out it was actually what is called a wiper. It pretended to be ransomware as a cover for the fact that it was exfiltrating all your data, and although it encrypted files, it never had a way for users to decrypt them or contact the gang about payments.
Mobile ransomware
It wasnt until the height of the infamous CryptoLocker and other similar families in 2014 that ransomware was seen on a large scale on mobile devices. Mobile ransomware typically displays a message that the device has been locked due to some type of illegal activity. The message states that the phone will be unlocked after a fee is paid. Mobile ransomware is often delivered via malicious apps, and requires that you boot the phone up in safe mode and delete the infected app in order to retrieve access to your mobile device.
Who do ransomware authors target?
When ransomware was introduced (and then re-introduced), its initial victims were individual systems (aka regular people). However, cybercriminals began to realize its full potential when they rolled out ransomware to businesses. Ransomware was so successful against businesses, halting productivity and resulting in lost data and revenue, that its authors turned most of their attacks toward them.
By the end of 2016, 12.3 percent of global enterprise detections were ransomware, while only 1.8 percent of consumer detections were ransomware worldwide. By 2017, 35 percent of small and medium-sized businesses had experienced a ransomware attack. Fast forward to the global pandemic in 2020, and the threat persists: Ransomware gangs attacked hospitals and medical facilities, and developed new tactics like double extortion, in which attackers are able to extort more money with threats to leak sensitive data than by decrypting computers they encrypted. Some ransomware groups offer their services to others, using a Ransomware-as-a-Service or RaaS model.
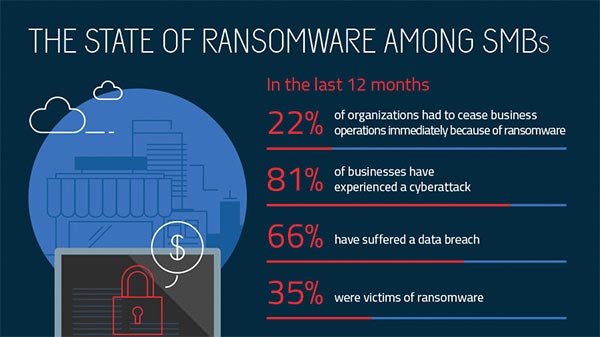
Ransomware report on small- and medium-sized businesses.
Geographically, ransomware attacks are still focused on western markets, with the UK, US, and Canada ranking as the top three countries targeted, respectively. As with other threat actors, ransomware authors will follow the money, so they look for areas that have both wide PC adoption and relative wealth. As emerging markets in Asia and South America ramp up on economic growth, expect to see an increase in ransomware (and other forms of malware) there as well.
How can I remove ransomware?
They say an ounce of prevention is worth a pound of cure. This is certainly true when it comes to ransomware. If an attacker encrypts your device and demands a ransom, theres no guarantee they will unencrypt it whether or not you pay up.
That is why its critical to be prepared before you get hit with ransomware. Two key steps to take are:
- Install security software before you get hit with ransomware
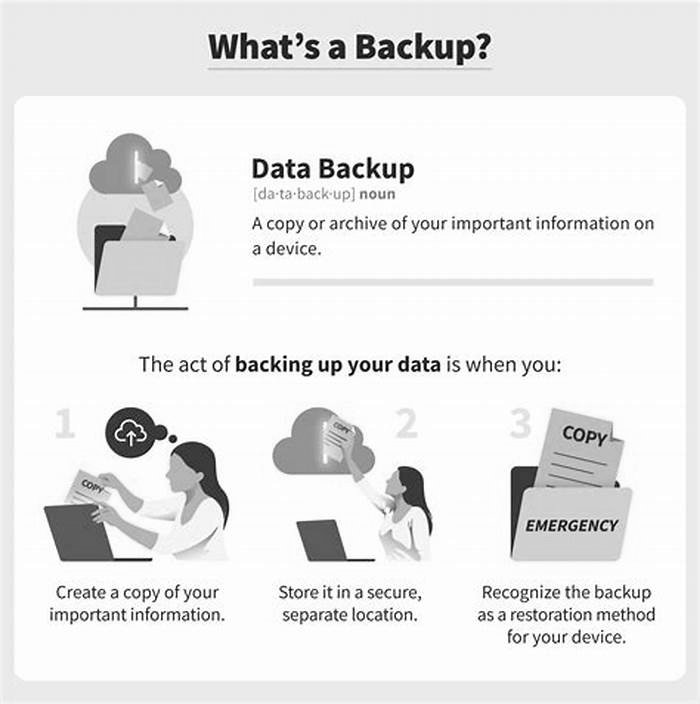
- Back up your important data (files, documents, photos, videos, etc.)
If you do find yourself with a ransomware infection, the number one rule is to never pay the ransom. (This is now adviceendorsed by the FBI.) All that does is encourage cybercriminals to launch additional attacks against either you or someone else.
One potential option for removing ransomware is that you may be able to retrieve some encrypted files by using free decryptors.To be clear: Not all ransomware families have had decryptors created for them, in many cases because the ransomware is utilizing advanced and sophisticated encryption algorithms.
And even if there is a decryptor, its not always clear if its for right version of the malware. You dont want to further encrypt your files by using the wrong decryption script. Therefore, youll need to pay close attention to the ransom message itself, or perhaps ask the advice of a security/IT specialist before trying anything.
Other ways to deal with a ransomware infection include downloading a security product known for remediation and running a scan to remove the threat. You may not get your files back, but you can rest assured the infection will be cleaned up. For screenlocking ransomware, a full system restore might be in order. If that doesnt work, you can try running a scan from a bootable CD or USB drive.
If you want to try and thwart an encrypting ransomware infection in action, youll need to stay particularly vigilant. If you notice your system slowing down for seemingly no reason, shut it down and disconnect it from the Internet. If, once you boot up again the malware is still active, it will not be able to send or receive instructions from the command and control server. That means without a key or way to extract payment, the malware may stay idle. At that point, download and install a security product and run a full scan.
However, these options for removing ransomware will not work in all cases. As noted above, for consumers, be proactive in your defense against ransomware by installing security software like Malwarebytes Premium, and by backing up all of your important data. For businesses, learn more about Malwarebytes business solutions that include ransomware detection, prevention, and rollback.
How do I protect myself from ransomware?
Security experts agree that the best way to protect from ransomware is to prevent it from happening in the first place.
Read about the best ways to prevent a ransomware infection.

While there are methods to deal with a ransomware infection, they are imperfect solutions at best, and often require much more technical skill than the average computer user. So heres what we recommend people do in order to avoid fallout from ransomware attacks.
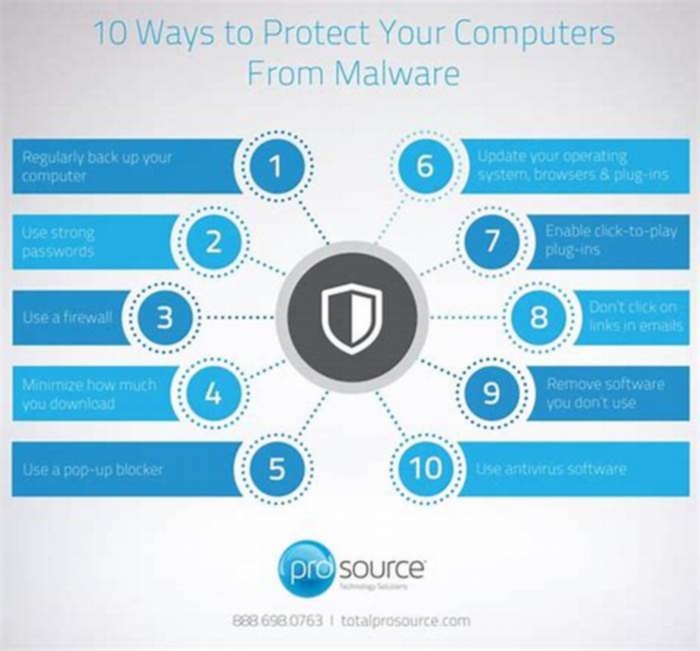
The first step in ransomware prevention is to invest in awesome cybersecuritya program with real-time protection thats designed to thwart advanced malware attacks such as ransomware. You should also look out for features that will both shield vulnerable programs from threats (an anti-exploit technology) as well as block ransomware from holding files hostage (an anti-ransomware component). Customers who were using the premium version of Malwarebytes for Windows, for example, were protected from all of the major ransomware attacks of 2017.
Next, as much as it may pain you, you need to create secure backups of your data on a regular basis. Our recommendation is to use cloud storage that includes high-level encryption and multiple-factor authentication. However, you can purchase USBs or an external hard drive where you can save new or updated filesjust be sure to physically disconnect the devices from your computer after backing up, otherwise they can become infected with ransomware, too.
Then, be sure your systems and software are updated. The WannaCry ransomware outbreak took advantage of a vulnerability in Microsoft software. While the company had released a patch for the security loophole back in March 2017, many folks didnt install the updatewhich left them open to attack. We get that its hard to stay on top of an ever-growing list of updates from an ever-growing list of software and applications used in your daily life. Thats why we recommend changing your settings to enable automatic updating.
Finally, stay informed. One of the most common ways that computers are infected with ransomware is through social engineering. Educate yourself (and your employees if youre a business owner) on how to detect malspam, suspicious websites, and other scams. And above all else, exercise common sense. If it seems suspect, it probably is.
How does ransomware affect my business?
GandCrab, SamSam, WannaCry, NotPetyatheyre all different types of ransomware and theyre hitting businesses hard. In fact, ransomware attacks on businesses went up 88% in the second half of 2018 as cybercriminals pivot away from consumer-focused attacks. Cybercriminals recognize big business translates to big payoffs, targeting hospitals, government agencies, and commercial institutions. All told, the average cost of a data breach, including remediation, penalties, and ransomware payouts, works out to $3.86 million.
The majority of ransomware cases as of late have been identified as GandCrab. First detected in January of 2018, GandCrab has already gone through several versions as the threat authors make their ransomware harder to defend against and strengthen its encryption. Its been estimated GandCrab has already raked in somewhere around $300 million in paid ransoms, with individual ransoms set from $600 to $700,000.
In another notable attack happening back in March of 2018, the SamSam ransomware crippled the City of Atlanta by knocking out several essential city servicesincluding revenue collection and the police record keeping system. All told, the SamSam attack cost Atlanta $2.6 million to remediate.
Considering the spate of ransomware attacks and the tremendous cost associated with them, now is a good time to get smart about protecting your business from ransomware. Weve covered the topic in great detail previously but heres a quick gloss on how to protect your business from malware.
- Backup your data. Assuming you have backups available, remediating a ransomware attack is as simple as wiping and reimaging infected systems. You may want to scan your backups to ensure they havent been infected, because some ransomware is designed to look for network shares. Accordingly, youd do well to store data backups on a secure cloud server with high-level encryption and multiple-factor authentication.
- Patch and update your software. Ransomware often relies on exploit kits to gain illicit access to a system or network (e.g. GandCrab). As long as the software across your network is up-to-date, exploit-based ransomware attacks cant hurt you. On that note, if your business runs on outdated or obsolete software then youre at risk for ransomware, because the software makers arent putting out security updates anymore. Get rid of abandonware and replace it with software still being supported by the manufacturer.
- Educate your end users on malspam and creating strong passwords. The enterprising cybercriminals behind Emotet are using the former banking Trojan as a delivery vehicle for ransomware. Emotet relies on malspam to infect an end user and get a foothold on your network. Once on your network, Emotet shows worm-like behavior, spreading from system to system using a list of common passwords. By learning how to spot malspam and implementing multi-factor authentication, youre end users will stay one step ahead of cybercriminals.
- Invest in good cybersecurity technology. Malwarebytes Endpoint Detection and Response, for example, gives you detection, response and remediation capabilities via one convenient agent across your entire network. You can also request a free trial of Malwarebytes anti-ransomware technologyto learn more specifically about our ransomware protection technology.
What do you do if youre already a victim of ransomware? No one wants to deal with ransomware after the fact.
- Check and see if there is a decryptor. In some rare cases you may be able to decrypt your data without paying, but ransomware threats evolve constantly with the aim of making it harder and harder to decrypt your files so dont get your hopes up.
- Dont pay the ransom. Weve long advocated not paying the ransom and the FBI (after some back and forth) agrees. Cybercriminals dont have scruples and theres no guarantee youll get your files back. Moreover, by paying the ransom youre showing cybercriminals that ransomware attacks work.
Keep up to date on the latest ransomware news in Malwarebytes Labs.
Malwarebytes anti-ransomware for business
Malwarebytes Endpoint Detection and Response delivers response options beyond just alerts, including proprietary Linking Engine Remediation and Ransomware Rollback.
Anti-Ransomware
Ransomware news
In 2022, ransomware continues to make headlines, from ransomware sent via USB sticks to ransomware that forced a jail to go on lockdown.Read the latest news on ransomware and ransomware attacks from Malwarebytes Labs:
2022 news
2021 news highlights
Anumber of major ransomware attacks made the news in 2021. Read Malwarebytes Labs take on some of the top stories from the year:
Ransomware podcasts
Lock and Code is Malwarebytes cybersecurity podcast. Listen to the latest episodes on ransomware:
History of ransomware attacks
The first ransomware, known as PC Cyborg or AIDS, was created in the late 1980s. PC Cyborg would encrypt all files in the C: directory after 90 reboots, and then demand the user renew their license by sending $189 by mail to PC Cyborg Corp. The encryption used was simple enough to reverse, so it posed little threat to those who were computer savvy.
With few variants popping up over the next 10 years, a true ransomware threat would not arrive on the scene until 2004, when GpCode used weak RSA encryption to hold personal files for ransom.
In 2007, WinLock heralded the rise of a new type of ransomware that, instead of encrypting files, locked people out of their desktops. WinLock took over the victim screen and displayed pornographic images. Then, it demanded payment via a paid SMS to remove them.
With the development of the ransom family Reveton in 2012 came a new form of ransomware: law enforcement ransomware. Victims would be locked out of their desktop and shown an official-looking page that included credentials for law enforcement agencies such as the FBI and Interpol. The ransomware would claim that the user had committed a crime, such as computer hacking, downloading illegal files, or even being involved with child pornography. Most of the law enforcement ransomware families required a fine be paid ranging from $100 to $3,000 with a pre-paid card such as UKash or PaySafeCard.
Average users did not know what to make of this and believed they were truly under investigation from law enforcement. This social engineering tactic, now referred to as implied guilt, makes the user question their own innocence and, rather than being called out on an activity they arent proud of, pay the ransom to make it all go away.
In 2013 CryptoLocker re-introduced the world to encrypting ransomwareonly this time it was far more dangerous. CryptoLocker used military grade encryption and stored the key required to unlock files on a remote server. This meant that it was virtually impossible for users to get their data back without paying the ransom.
This type of encrypting ransomware is still in use today, as its proven to be an incredibly effective tool for cybercriminals to make money. Large scale outbreaks of ransomware, such as WannaCry in May 2017 and Petya in June 2017, used encrypting ransomware to ensnare users and businesses across the globe.
In late 2018, Ryuk burst onto the ransomware scene with a slew of attacks on American news publications as well as North Carolinas Onslow Water and Sewer Authority. In an interesting twist, targeted systems were first infected with Emotet or TrickBot, two information stealing Trojans now being used to deliver other forms of malware like Ryuk, for instance. Director of Malwarebytes Labs, Adam Kujawa speculates that Emotet and TrickBot are being used to find high-value targets. Once a system is infected and flagged as a good target for ransomware, Emotet/TrickBot re-infects the system with Ryuk.
In 2019, the criminals behind the Sodinokibi ransomware (an alleged offshoot of GandCrab) have started to use managed service providers (MSP) to spread infections. In August of 2019, hundreds of dental offices around the country found they could no longer access their patient records. Attackers used a compromised MSP, in this case a medical records software company, to directly infect upwards of 400 dental offices using the record keeping software.
Also in 2019, Malwarebytes discovered the Maze family of ransomware. According to Malwarebytes 2021 State of Malware Report, Maze went beyond holding data hostageit included an additional threat of publicly releasing swiped data if a ransom went unpaid. Another ransomware gang that first appeared the same year is the REvil, also known as Sodin or Sodinokibi. A sophisticated ransomware gang, REvil uses a Ransomware-as-a-Service (RaaS) model to sell to others who want to use their software to commit ransomware attacks.
In 2020, yet another new family of ransomware named Egregor came on the scene. Its thought to be somewhat of a successor to the Maze ransomware family, as many of the cybercriminals who worked with Maze changed over to Egregor. Similar to Maze, Egregor uses a double extortion attack, in which they both encrypt files and steal data from the victim that they threaten to publish online unless the ransom is paid.
While ransomware attacks toward individuals have been a problem for several years, ransomware attacks on businesses, hospitals and health care systems, schools and school districts, local governments, and other organizations havebeen making headlines in 2021. From Colonial Pipeline to large meatpacker JBS to Steamship Authority, the largest ferry service in Massachusetts, ransomware attackers have shown that they are able and willing to disrupt large companies that provide everyday goods like gasoline, food, and transportation.
Throughout2021, we have seen headline after headline of large ransomware attacks on major companies and organizations (see the news section above to read about many of them). Mid-year, the US government said that ransomware was to be investigated like terrorism, and created the website StopRansomware.gov to bring together information on stopping and surviving ransomware attacks.
What will the rest of 2021 and 2022 bring in the ransomware threat landscape? While we dont know, we will be here to keep you informed. Check back to this page for future updates, and follow the Malwarebytes Labs blog for the latest in cybersecurity news.