Guide to Securing Your Smart Home Devices from Cyber Threats
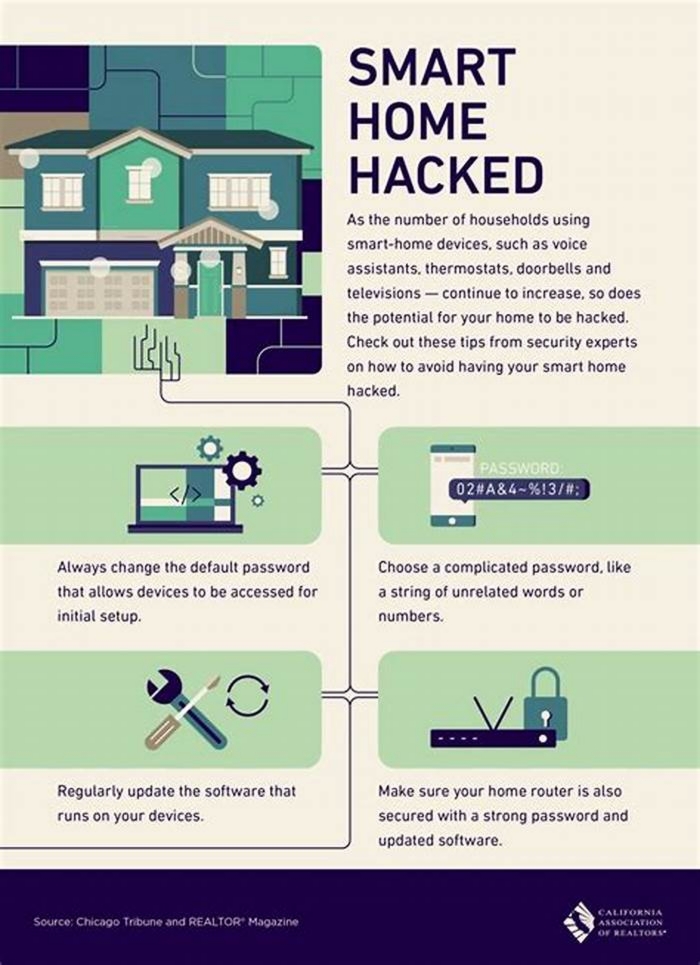
How To Secure Your Smart Home Devices
Introduction
Welcome to the world of smart home devices, where you can control your lights, appliances, security systems, and more with just a tap on your smartphone or a voice command. With the rapid advancement of technology, smart homes have become increasingly popular, providing convenience, comfort, and efficiency to homeowners. However, as we embrace the convenience of these devices, its crucial to prioritize their security.
Smart home devices are vulnerable to cyber threats, just like any other connected device. From potential hackers gaining access to your home network to compromising your privacy through unauthorized access to cameras or microphones, the risks are real. Thats why its essential to understand the potential dangers and take proactive measures to secure your smart home devices.
In this article, we will explore a range of strategies and best practices to help you safeguard your smart home devices from cybersecurity threats. By implementing these measures, you can enjoy the benefits of a connected home without sacrificing your security and peace of mind.
Understand the Risks of Smart Home Devices
Before diving into securing your smart home devices, its essential to understand the potential risks involved. By having a solid grasp of these risks, you can make informed decisions and take appropriate actions to mitigate them. Here are some key risks to be aware of:
1. Data Privacy: Smart home devices collect a vast amount of personal data, including your daily routines, living patterns, and potentially sensitive information. If this data falls into the wrong hands, it can be used for identity theft or other malicious purposes. Therefore, its crucial to be mindful of how your data is stored, transmitted, and shared by your devices and choose devices that prioritize data privacy.
2. Unauthorized Access: Hackers may attempt to gain unauthorized access to your smart home devices and control them remotely. This can result in breaches of privacy, tampering with security systems, or even physical harm if connected to critical home functions like locks or surveillance systems. Understanding the security features of your devices and implementing additional measures to enhance protection can help mitigate these risks.
3. Insecure Communication: Smart home devices communicate with each other and with external servers through various protocols, such as Wi-Fi, Bluetooth, or Zigbee. If these communications are not adequately secured, they can be intercepted by hackers, potentially compromising your entire network. Ensuring secure communication protocols and strong encryption standards are in place is crucial to maintain the integrity of your smart home ecosystem.
4. Lack of Manufacturer Updates: Many smart home devices receive periodic firmware updates from manufacturers to fix vulnerabilities and improve security. However, some manufacturers may not provide regular updates or cease support for older devices, leaving them vulnerable to known exploits. Keeping your devices updated and choosing reputable manufacturers who prioritize security can help minimize this risk.
5. Third-Party Integrations: Smart home devices often integrate with third-party services and applications, such as voice assistants or remote monitoring platforms. While these integrations can enhance functionality, they can also introduce additional security vulnerabilities if not properly secured. Reviewing the security practices of third-party integrators and only allowing trusted and reputable services to access your devices can mitigate this risk.
By understanding these risks, you can take the necessary steps to protect your smart home devices from potential threats. In the following sections, we will explore some practical strategies and best practices to enhance the security of your smart home ecosystem.
Choose Secure Smart Home Devices
When building your smart home ecosystem, its crucial to choose devices from reputable manufacturers that prioritize security. Here are some factors to consider when selecting secure smart home devices:
1. Research the Manufacturer: Before purchasing any smart home device, research the manufacturers reputation for security. Look for companies that have a track record of prioritizing security, providing regular updates, and promptly addressing security vulnerabilities.
2. Read Product Reviews: Reading reviews from trusted sources and other users can provide insights into the security features and vulnerabilities of specific devices. Pay attention to any known security issues or concerns raised by other users.
3. Check for Security Certifications: Look for smart home devices that have been certified by recognized security standards organizations, such as the Wi-Fi Alliance, Zigbee Alliance, or UL (Underwriters Laboratories). These certifications indicate that the devices have undergone rigorous testing to meet specific security standards.
4. Assess Device Security Features: Consider the security features offered by the devices youre interested in. Look for features like secure encryption protocols, two-factor authentication, and automatic security updates. Devices that prioritize security should have built-in measures to protect against common cybersecurity threats.
5. Compatibility with Security Platforms: Ensure that the smart home devices you choose are compatible with reputable security platforms or services. Integrating your devices with a trusted security hub or service can provide an additional layer of protection and centralized control over your smart home ecosystem.
6. Consider Open-Source Options: Open-source smart home platforms and devices often have active security communities and frequent updates to address vulnerabilities. While these may require more technical knowledge, they can provide greater transparency and customization options for security-conscious users.
By choosing secure smart home devices, you can significantly reduce the risk of cyber threats and enjoy a more secure and reliable smart home ecosystem. Remember to keep yourself updated on the latest security concerns and seek devices that prioritize ongoing security enhancements.
Keep Your Devices Updated
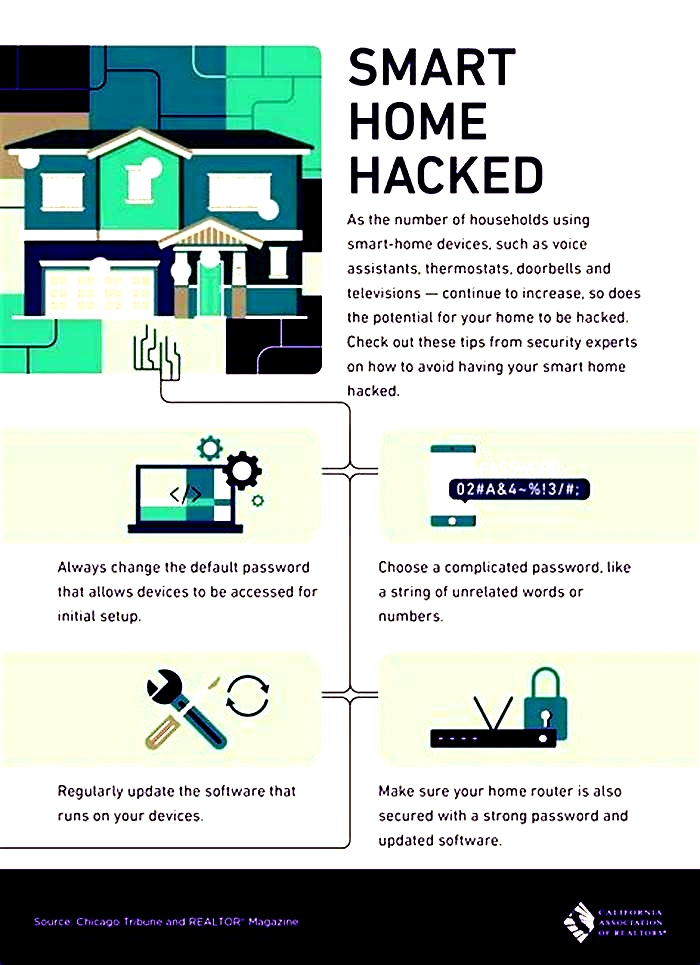
One of the most important steps in ensuring the security of your smart home devices is to keep them updated with the latest firmware and software updates. Manufacturers continually release updates to address security vulnerabilities and improve device performance. Heres why keeping your devices updated is crucial:
1. Patch Security Vulnerabilities: Cybercriminals constantly search for vulnerabilities in smart home devices to exploit. By keeping your devices updated, you can ensure that any known security vulnerabilities are patched, reducing the risk of unauthorized access or compromise.
2. Enhance Device Performance: Firmware and software updates not only address security issues but also often include performance enhancements and new features. By regularly updating your devices, you can ensure that they function optimally and take advantage of the latest improvements.
3. Receive New Security Features: Manufacturers often introduce new security features through updates to enhance the overall security of their devices. These may include stronger encryption protocols, improved authentication mechanisms, or additional layers of protection against emerging threats. By updating your devices, you can benefit from these enhanced security measures.
4. Compatibility with Ecosystem Updates: Many smart home devices operate within a larger ecosystem, such as a hub or central control system. Updates to these ecosystem components may require corresponding updates to individual devices for seamless compatibility and improved security. Regularly updating your devices ensures that they remain compatible with the broader smart home ecosystem.
5. Automate Updates: To simplify the update process, consider enabling automatic updates when available. This ensures that your devices receive the latest security patches without requiring manual intervention. However, its still important to periodically check and verify that updates are being applied successfully.
6. Check for End-of-Support: Manufacturers may discontinue support for older devices after a certain period. This means that they will no longer release updates or security patches for those devices. Its essential to be aware of the support lifecycle and consider replacing unsupported devices with newer, more secure alternatives.
By prioritizing regular updates, you can significantly reduce the risk of security breaches, enhance device performance, and ensure ongoing compatibility within your smart home ecosystem. Make it a habit to check for updates regularly and apply them promptly for all your connected devices.
Create Strong and Unique Passwords
Creating strong and unique passwords for your smart home devices is crucial to prevent unauthorized access and protect your data. Weak or reused passwords make it easier for hackers to gain control of your devices and potentially compromise your entire smart home ecosystem. Here are some best practices to follow when creating passwords:
1. Use Complex Passwords: Avoid using simple and predictable passwords. Instead, create passwords that consist of a combination of uppercase and lowercase letters, numbers, and special characters. The longer and more complex the password, the more secure it is.
2. Avoid Common Passwords: Stay away from commonly used passwords such as 123456 or password. These passwords are easily guessable and provide little to no protection. Use a unique combination of characters that would be difficult for anyone to guess.
3. Dont Reuse Passwords: Each of your smart home devices should have a unique password. Reusing passwords across multiple devices or online accounts can be risky, as a breach in one device or account could compromise all of them. Use a password manager to help remember and generate unique passwords for each device.
4. Change Default Passwords: Many smart home devices come with default passwords set by the manufacturer. Change these passwords immediately upon installation to something strong and unique. Default passwords are often well-known among hackers, making it easier for them to gain unauthorized access.
5. Update Passwords Regularly: Set a schedule to update your passwords periodically. This practice reduces the risk of long-term exposure and ensures that compromised passwords are changed promptly. Aim to update passwords at least every three to six months.
6. Consider Password Phrases: Instead of relying on a single word as your password, consider using a passphrase. A passphrase is a series of words or a sentence that is easy for you to remember but difficult for others to guess. For example, correct horse battery staple is more secure than a single word password.
7. Enable Biometric Authentication: Where possible, utilize biometric authentication methods such as fingerprints or facial recognition for your smart home devices. Biometrics provide an added layer of security and convenience, removing the need to rely solely on passwords.
By following these password best practices, you can significantly enhance the security of your smart home devices. Remember, a strong and unique password is your first line of defense against potential cyber threats. Take the time to create and update passwords regularly to ensure the safety of your smart home ecosystem.
Set Up Two-Factor Authentication
Two-Factor Authentication (2FA) adds an extra layer of security to your smart home devices by requiring a second form of verification in addition to your password. It helps protect against unauthorized access even if your password is compromised. Heres why setting up 2FA is essential:
1. Increased Security: 2FA provides an added layer of security by requiring a second factor, such as a unique code sent to your mobile device or a biometric scan, to verify your identity. Even if a hacker manages to obtain your password, they will still need the second factor to gain access to your smart home devices.
2. Off-Limits to Hackers: With 2FA enabled, even if someone has your password, they wont be able to access your smart home without the additional verification factor. This additional security measure helps safeguard your devices, data, and personal privacy from unauthorized individuals.
3. Quick and Easy Setup: Many smart home devices and associated applications provide the option to enable 2FA. It usually involves a one-time setup process where you link your account to a trusted device or app. Once enabled, you will receive a unique code or prompt for verification whenever you attempt to log in.
4. Multiple Authentication Methods: 2FA offers various authentication methods, depending on the device or application. This can include SMS text messages, authenticator apps, email verification, or biometric authentication. Choose the method that is most convenient and secure for you.
5. Compatibility with Multiple Devices: Smart home devices can often be accessed from multiple devices, such as smartphones, tablets, or computers. With 2FA enabled, each device will require its own unique verification, ensuring that only authorized users can access and control your smart home ecosystem.
6. Peace of Mind: By enabling 2FA, you can have peace of mind knowing that your smart home devices are better protected against unauthorized access. It adds an extra layer of security to your overall smart home ecosystem and helps prevent potential vulnerabilities.
Remember to review the instructions provided by the manufacturer or app developer to properly set up 2FA for each of your smart home devices. Take the time to enable this additional security measure, as it significantly enhances the protection of your smart home ecosystem and personal privacy.
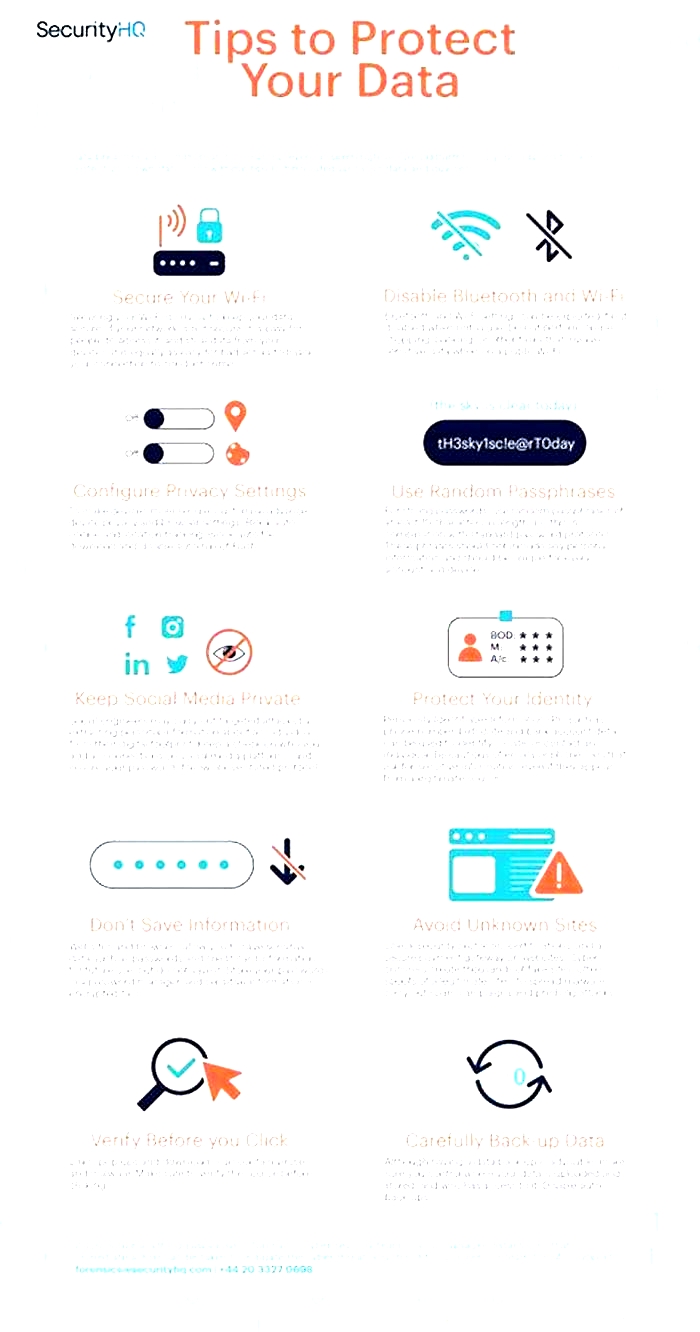
Secure Your Wi-Fi Network
Your home Wi-Fi network serves as the foundation for your smart home ecosystem. Its crucial to secure your Wi-Fi network to prevent unauthorized access to your devices and data. Here are some essential steps to secure your Wi-Fi network:
1. Change the Default Network Name (SSID): The default network name (SSID) assigned by your router may reveal the manufacturer or model, making it easier for hackers to identify vulnerabilities. Change the SSID to a unique name that does not personally identify yourself or provide any hints about your network.
2. Create a Strong Network Password: Set a strong, complex password for your Wi-Fi network. Use a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using common words or personal information that can be easily guessed. A strong password will make it harder for unauthorized individuals to gain access to your network.
3. Enable Network Encryption: Use the latest encryption protocol supported by your router, such as WPA2 or WPA3. Encryption helps protect your network communications by encoding data sent between devices. Ensure that older encryption protocols, such as WEP, are disabled, as they are no longer secure.
4. Change Router Admin Password: Your router has an administrative interface that allows you to configure settings. Change the default administrative password to a strong and unique one. This prevents unauthorized individuals from accessing and modifying your router settings.
5. Disable Remote Management: Remote management allows you to access your routers settings from outside your home network. Disable this feature unless you specifically need it, as it can create a possible entry point for attackers. If remote management is necessary, enable it only for specific IP addresses or use a virtual private network (VPN) for secure remote access.
6. Enable Network Firewall: Most routers have built-in firewalls that help protect against external threats. Ensure that your routers firewall is enabled to monitor and filter incoming and outgoing traffic. It acts as a barrier between your network and the internet, blocking malicious activities.
7. Hide Your Network: Disable the broadcasting of your Wi-Fi networks SSID, also known as hiding your network. This makes it less visible to potential attackers. However, note that experienced attackers can still discover hidden networks. The main benefit is reducing the chances of casual users connecting to your network unknowingly.
8. Regularly Update Router Firmware: Check for firmware updates for your router regularly. Router manufacturers release updates that address security vulnerabilities and improve performance. Keep your routers firmware up to date to ensure you have the latest security patches.
By following these steps, you can significantly increase the security of your Wi-Fi network. Securing your network is a crucial step in protecting your smart home devices and ensuring the privacy of your data. Take the time to implement these measures and regularly review your network security settings.
Disable Unnecessary Features
When it comes to securing your smart home devices, its essential to disable any unnecessary features or services that may pose potential security risks. By only enabling the features you truly need and disabling the rest, you can minimize the attack surface and reduce the chances of unauthorized access. Here are some steps to disable unnecessary features:
1. Review Default Settings: Carefully examine the default settings of your smart home devices. Manufacturers often enable certain features by default to enhance convenience or compatibility, but these features may not be essential to your specific needs. Disable any default settings that you dont require.
2. Disable Universal Plug and Play (UPnP): UPnP is a convenient feature that allows devices to automatically discover and communicate with each other on your network. However, it can also expose vulnerabilities, making it easier for attackers to gain access to your devices. Disable UPnP in your router settings if you dont specifically need it.
3. Close Unused Ports: Smart home devices may have open network ports for various purposes, such as remote access or firmware updates. Review the documentation or manufacturers instructions to identify unused ports and close them via your routers settings. Closing unnecessary ports reduces the potential entry points for attackers.
4. Disable Remote Access: Many smart home devices offer a remote access feature, allowing you to control them from anywhere. However, this convenience can also expose your devices to potential security risks if not properly secured. Disable remote access unless you explicitly need it, and consider using a VPN (Virtual Private Network) for secure remote access if available.
5. Turn Off Guest Networks: Guest networks are separate Wi-Fi networks that allow visitors to connect to your network without accessing your main network. While convenient, guest networks can also introduce security risks if not properly managed. Disable guest networks when not in use to reduce the potential for unauthorized access or misuse.
6. Disable Unused Smart Features: Some smart home devices come with additional smart features that you may not use regularly. These features often require additional permissions or integration with third-party services, increasing the potential attack surface. Disable any smart features that you dont need or use to minimize potential security risks.
7. Limit App Permissions: Review the permissions granted to smart home apps on your mobile devices. Some apps may request excessive permissions that they dont actually need. Limit app permissions to only those necessary for their proper functionality, reducing the risk of unauthorized access to your personal data or devices.
8. Regularly Update Device Firmware: Keep your smart home devices updated with the latest firmware provided by the manufacturers. Firmware updates often include security patches and improvements that address vulnerabilities. Regularly check for and install firmware updates to ensure you are running the most secure version of each device.
By disabling unnecessary features and services, you can minimize potential security risks within your smart home ecosystem. Take the time to review each devices settings and assess the necessity of each feature. Remember, a streamlined and secure setup will help protect your devices and ensure the privacy and security of your smart home.
Create a Guest Network
Creating a separate guest network for your smart home can provide an extra layer of security and privacy for both you and your visitors. A guest network allows guests to connect to the internet without accessing your main network, protecting your sensitive data and smart devices. Heres why you should consider setting up a guest network:
1. Segregation of Network Traffic: By creating a guest network, you separate your main network from your guests devices. This segregation prevents guests from accessing your smart home devices and data, reducing the risk of unauthorized access or potential intrusion.
2. Protection of Personal Data: A guest network ensures that your guests devices are isolated from your home devices, protecting your personal data. This prevents unauthorized access to shared files, printers, or other network resources that are exclusive to your main network.
3. Enhanced Network Security: Guests devices may have various security vulnerabilities, such as outdated software or weak passwords. By isolating them on a guest network, any potential security breaches or intrusions will be limited to that network, minimizing the impact on your main network and devices.
4. Reduction in Network Congestion: Guests devices can consume bandwidth and resources, potentially impacting the performance of your main network. By directing them to a separate guest network, you ensure that your own devices have sufficient resources for optimal performance.
5. Control over Network Permissions: With a guest network, you have control over network permissions. You can set limits on the bandwidth allocation for guest devices, regulate access to certain websites or services, and apply additional security measures specific to the guest network.
6. Ease of Access for Guests: A guest network provides a hassle-free and secure way for guests to access the internet without needing to share your main network password. You can provide a separate network name (SSID) and password specifically for guests, making it easy for them to connect and stay connected during their visit.
7. Simplified Network Management: A guest network simplifies network management by allowing you to focus on your main network. You can troubleshoot issues and monitor network activity in a more streamlined manner, knowing that your guests devices are separated and isolated from your critical network infrastructure.
Consult your routers user manual or interface to set up a guest network. Typically, youll find the option to create a guest network under the Wi-Fi settings or advanced network settings. Configure the guest network with a unique SSID and password, and adjust any additional settings or access restrictions as desired.
By creating a guest network, you can provide a convenient and secure internet experience for your guests while protecting your main network and smart devices. Take advantage of this feature to enhance your smart homes overall privacy and security.
Use a Firewall
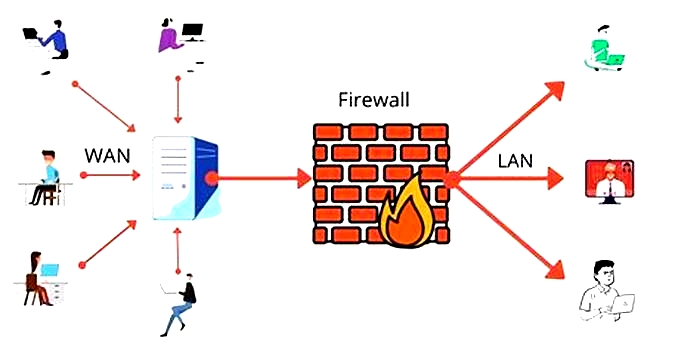
Using a firewall is an essential component of your smart homes security infrastructure. A firewall acts as a barrier between your network and the outside world, monitoring and filtering incoming and outgoing network traffic. It helps protect your smart home devices from unauthorized access and potential cyber threats. Heres why using a firewall is crucial for securing your smart home:
1. Network Protection: A firewall serves as the first line of defense for your network, blocking unauthorized access attempts from external sources. It examines incoming and outgoing data packets, allowing only legitimate traffic to pass through and keeping potential attackers at bay.
2. Intrusion Detection and Prevention: A firewall can detect and prevent unauthorized access attempts or suspicious activities within your network. It monitors network traffic patterns, identifying potential intrusions or malicious behavior, and takes appropriate action to block or alert you of any potential threats.
3. Traffic Filtering: Firewalls allow you to set up rules and filters to control the flow of network traffic. You can specify which devices or applications have access to certain ports, protocols, or IP addresses, reducing the attack surface and ensuring that only authorized connections are allowed. This helps prevent unauthorized access or data exfiltration.
4. Protection Against Malware and Viruses: Some advanced firewalls include built-in antivirus and malware detection capabilities. They can analyze incoming and outgoing data packets for signs of malicious activity, blocking known threats and preventing them from compromising your network and devices.
5. Control Over Outbound Connections: Firewalls provide you with granular control over outbound connections from your smart home devices. You can restrict specific devices or applications from establishing connections to potentially risky or untrusted sources, preventing data leaks or unauthorized data transfers.
6. Safe Remote Access: If you require remote access to your smart home devices, using a firewall with VPN capabilities adds an extra layer of security. With a VPN (Virtual Private Network), you can establish an encrypted connection to your home network, ensuring that any remote access is secure and protected from potential eavesdropping or unauthorized access.
7. Centralized Security Management: Many modern firewalls come with centralized management interfaces, allowing you to monitor and control the security of your smart home devices from a single dashboard. This makes it easier to identify and respond to potential security threats, saving you time and effort in managing your network security.
Choose a firewall that is compatible with your network infrastructure and meets your specific security requirements. Depending on your needs, you can opt for hardware firewalls that sit between your router and devices or software firewalls that run directly on your devices or routers.
By implementing a firewall, you can establish robust protection for your smart home devices, safeguarding them from potential malicious activities and unauthorized access. Regularly update your firewall firmware and settings to ensure you are utilizing the latest security features and best practices.
Keep Your Mobile Devices Secure
Mobile devices play a critical role in managing and controlling your smart home ecosystem. Its vital to keep your smartphones and tablets secure to protect your personal information, control access to your smart home devices, and prevent potential security breaches. Here are key measures to ensure the security of your mobile devices:
1. Use Strong Device Locks: Set a strong passcode, PIN, or biometric authentication (such as fingerprint or facial recognition) to secure your mobile device. This adds an extra layer of protection and guards against unauthorized access if your device ever gets lost or stolen.
2. Enable Device Encryption: Encrypting your mobile devices storage ensures that your data remains secure, even if the device falls into the wrong hands. Enable device encryption through the settings on your device to protect sensitive information stored locally on your device.
3. Keep Software and Apps Up to Date: Regularly update your mobile devices operating system, as well as the apps installed on it. Software updates often include security patches and bug fixes that address vulnerabilities. Staying up to date minimizes the risk of exploitation by cybercriminals.
4. Download Apps from Trusted Sources: Only download apps from official app stores such as Google Play Store or Apple App Store. These stores have security measures in place to detect and remove malicious apps. Avoid downloading apps from third-party sources, as they may contain malware or other security risks.
5. Be Mindful of App Permissions: Review and consider the permissions requested by apps during installation. Be cautious when granting access to personal data, contacts, or device features. Evaluate whether the requested permissions align with the apps intended functionality and requirement. Restrict app permissions if necessary.
6. Use Mobile Security Software: Install reputable mobile security software that provides features such as malware detection, anti-theft measures, and secure browsing. These software packages offer additional layers of protection for your mobile device and data.
7. Enable Remote Device Management: Take advantage of mobile device management features, such as Find My iPhone (iOS) or Find My Device (Android). These tools help track, lock, and erase your device remotely if it gets lost or stolen, minimizing the risk of unauthorized access to your smart home ecosystem.
8. Be Wary of Wi-Fi Networks: Avoid connecting to unsecured or unknown Wi-Fi networks, especially when accessing your smart home devices remotely. Public Wi-Fi networks are often unsecure and may expose your sensitive information to potential eavesdropping or hacking attempts. Use a VPN (Virtual Private Network) for secure remote access when needed.
By implementing these measures, you can enhance the security of your mobile devices and protect your smart home ecosystem from potential security breaches. Safeguarding your mobile devices ensures that you have control over your smart home and minimizes the risk of unauthorized actions or access by malicious individuals.
Encrypt Your Network Traffic
Encrypting your network traffic is an essential step in securing your smart home ecosystem. Encryption converts your data into a coded form that can only be decoded by authorized devices, ensuring that sensitive information remains protected from prying eyes and potential threats. Heres why encrypting your network traffic is crucial:
1. Data Confidentiality: Encryption ensures that your network traffic, including communication between devices and data transmitted over the internet, is protected from unauthorized access. It prevents anyone from intercepting and deciphering your data, maintaining its confidentiality.
2. Protection Against Eavesdropping: Encryption thwarts potential eavesdroppers who may attempt to intercept your network traffic to gather sensitive information. It safeguards your data, such as login credentials, financial details, or personal communications, from being acquired by malicious individuals.
3. Securing Remote Access: If you access your smart home devices remotely, encrypting your network traffic is critical. It ensures that your communication with your devices is encrypted, protecting your commands and data from being compromised during transit over the internet.
4. Wi-Fi Security: Encrypting your Wi-Fi network traffic protects it from unauthorized access by encrypting the data transmitted between your devices and the router. This prevents potential attackers from inspecting your internet activities or gaining unauthorized access to your smart home devices.
5. Secure Authentication: Encryption plays a vital role in ensuring secure authentication processes. When you log in to your smart home devices or access your smart home hub, encryption safeguards your login credentials, making it significantly more challenging for attackers to intercept and decipher them.
6. Utilize Encryption Protocols: Use encryption protocols such as WPA2 (Wi-Fi Protected Access 2) or WPA3 for securing your Wi-Fi network. These protocols provide robust encryption algorithms and mechanisms to protect your network traffic from potential intruders. Ensure that your devices and router support and utilize the latest encryption standards.
7. Employ End-to-End Encryption: For remote access and communication with your smart home devices, opt for services and platforms that utilize end-to-end encryption. End-to-end encryption ensures that your communication is encrypted from the sender to the receiver without any intermediary being able to decipher the content.
8. Virtual Private Network (VPN) Usage: Consider using a VPN to encrypt your internet traffic when accessing your smart home devices remotely. A VPN creates a secure and encrypted tunnel between your device and the network, protecting your data from potential eavesdropping or hacking attempts.
By encrypting your network traffic, you add an extra layer of security to your smart home ecosystem. It safeguards your data, communications, and interactions with your devices, reducing the risk of unauthorized access and ensuring the privacy and integrity of your smart home network.
Disable Remote Access
Disabling remote access to your smart home devices is an important step in securing your smart home ecosystem. While remote access allows you to control your devices from anywhere, it also introduces potential security risks. Heres why disabling remote access is crucial for your smart home security:
1. Minimize Remote Attack Surface: Disabling remote access reduces the attack surface by preventing potential attackers from gaining unauthorized access to your smart home devices. It limits the potential entry points that hackers can exploit, thereby reducing the risk of unauthorized control or tampering.
2. Protection against Remote Exploits: Some smart home devices may have vulnerabilities that can be exploited remotely, allowing attackers to gain control over the devices. By disabling remote access, you prevent attackers from leveraging these vulnerabilities to compromise your smart home ecosystem.
3. Prevent Unintentional Misconfiguration: Remote access can potentially lead to unintentional misconfiguration if accessed by individuals who are not familiar with your devices. This misconfiguration may unintentionally expose your devices or network to security risks. Disabling remote access helps prevent such unintended misconfigurations.
4. Enhanced Privacy: Disabling remote access mitigates potential privacy risks associated with remote connections. It ensures that your smart home devices, particularly those with cameras or microphones, cannot be accessed remotely without your consent, protecting your privacy and that of your family.
5. Secure Access through Local Network: By disabling remote access, you limit control of your smart home devices to your local network only. This means that access to your devices requires physical presence within your home or connection to your Wi-Fi network, significantly reducing the risk of unauthorized control or manipulation.
6. Utilize Local Control Hubs: If you still desire remote control capabilities, consider using local control hubs that allow secure remote access through a VPN (Virtual Private Network). These hubs provide an encrypted connection between your remote device and your home network, ensuring secure access while minimizing potential security risks.
7. Evaluate Specific Needs: Assess your specific needs for remote access. If you find that remote control of your smart devices is not necessary or rarely utilized, disabling remote access can be a proactive security measure to safeguard your smart home ecosystem.
8. Follow Manufacturer Recommendations: Check the recommendations provided by the manufacturers of your smart home devices. They may have specific guidelines or advice on securing remote access. Follow their recommendations to ensure that you are implementing the best practices for remote access security.
Remember, disabling remote access may limit some conveniences, such as controlling your devices when youre away from home. However, prioritizing security by disabling remote access helps prevent potential security breaches and ensures that you have full control over your smart home devices and their interactions with the outside world.
Secure Your Smart Home Hub
Your smart home hub is the central control point for your smart home ecosystem, making it a crucial component to secure. By implementing security measures specific to your smart home hub, you can protect your entire smart home network and devices. Heres how to secure your smart home hub:
1. Change Default Passwords: Many smart home hubs come with default login credentials. Change these default passwords immediately to strong and unique ones. This prevents unauthorized access to your hub and ensures that only authorized individuals can control and manage your smart home ecosystem.
2. Keep Hub Firmware Up to Date: Regularly check for firmware updates provided by the manufacturer for your smart home hub. Firmware updates often include security patches and performance improvements. Keeping your hubs firmware up to date helps close any known vulnerabilities and ensures optimal security.
3. Enable Two-Factor Authentication: If your smart home hub supports two-factor authentication (2FA), enable this additional layer of security. 2FA requires a secondary verification method, such as a unique code sent to your mobile device, for logging into your hub. It adds an extra layer of protection against unauthorized access.
4. Segment Your Network: Consider segmenting your smart home hub on a separate network or VLAN (Virtual Local Area Network) to isolate it from other devices on your home network. This segregation helps contain potential security breaches and limits unauthorized access to your smart home devices.
5. Protect Hub with a Firewall: Utilize a firewall, either as part of your smart home hub or through your network router, to protect your hub from unwanted network traffic and potential intrusion attempts. Configure the firewall to allow access only to necessary services and ports, while blocking all others.
6. Secure Wi-Fi Network: Ensure that your Wi-Fi network, through which your smart home hub communicates with devices, is properly secured. Follow best practices such as changing default Wi-Fi network names (SSIDs), using strong wireless encryption protocols like WPA2 or WPA3, and regularly updating Wi-Fi network passwords.
7. Regularly Back Up Hub Settings: Periodically back up your smart home hubs settings, configurations, and automation routines. In the event of a device failure or software update, having a backup ensures that you can quickly restore your hub and minimize downtime without losing important settings or customizations.
8. Monitor Hub Activity: Keep a watchful eye on your smart home hubs activity. Regularly review logs and audit logs provided by the hubs management interface to look for any suspicious activities or unauthorized access attempts. Promptly investigate any anomalies and take appropriate actions to address them.
By following these security measures, you can fortify the security of your smart home hub and protect your entire smart home ecosystem. The hub serves as the central control point, so securing it ensures that your devices, data, and smart home automation remain protected from potential threats.
Secure Your Bluetooth Devices
Bluetooth technology is widely used in smart home devices to enable wireless communication and connectivity. However, it is crucial to secure your Bluetooth devices to prevent unauthorized access and potential privacy breaches. Here are key steps to secure your Bluetooth devices:
1. Keep Bluetooth Devices Updated: Regularly check for firmware updates provided by the manufacturers of your Bluetooth devices. Updates often include security patches and bug fixes that address vulnerabilities. Keeping your devices updated helps ensure optimal security.
2. Disable Bluetooth When Not in Use: Turn off Bluetooth on your devices when youre not actively using it. Leaving Bluetooth enabled for extended periods increases the chances of unauthorized pairing or hijacking. Disabling Bluetooth when not needed mitigates potential risks and preserves battery life.
3. Secure Pairing: Enable secure pairing options on your Bluetooth devices whenever possible. This typically involves using a password or PIN to authenticate the pairing process, ensuring that only authorized devices can connect to your Bluetooth device.
4. Use Unique Device Names: Change the default names of your Bluetooth devices to unique identifiers that dont reveal device types or manufacturers. Using generic or easily identifiable names can make it easier for potential attackers to target your devices.
5. Limit Device Visibility: Set your Bluetooth devices to non-discoverable mode by default. Enable discoverability only when necessary, and ensure that you are aware of any incoming connection requests before accepting them. This prevents random devices from attempting to connect to your devices without your knowledge.
6. Establish Trusted Connections: Configure your devices to only connect to trusted and authorized devices. Restrict the automatic pairing feature and manually verify and authorize each connection request. This prevents unauthorized devices from gaining access to your Bluetooth network.
7. Be Cautious in Public Places: Exercise caution when using Bluetooth devices in public areas where potential attackers may attempt to exploit Bluetooth vulnerabilities. Be vigilant for any suspicious connection attempts or unfamiliar devices trying to pair without your consent.
8. Monitor Device Pairings: Regularly review the list of paired devices on your Bluetooth devices and remove any unused or unrecognized entries. This ensures that only authorized devices retain access to your Bluetooth network.
9. Consider Bluetooth Range: Bluetooth signals have a limited range, but they can still extend outside your home. Be mindful of the range and position your devices accordingly to minimize the risk of unauthorized connections from nearby locations.
10. Utilize Additional Security Measures: If available, take advantage of additional security measures provided by your Bluetooth devices, such as encryption or password protection for data transfers. These features add another layer of protection to keep your Bluetooth communications secure.
By implementing these security measures, you can enhance the protection of your Bluetooth devices and minimize the risk of unauthorized access or data breaches. Securing your Bluetooth devices ensures the privacy and integrity of your smart home ecosystem.
Be Cautious of IoT-Enabled Cameras and Microphones
IoT-enabled cameras and microphones can greatly enhance the functionality and convenience of your smart home. However, its vital to exercise caution and take necessary precautions to protect your privacy and prevent potential security breaches. Heres why you should be cautious of these devices:
1. Privacy Concerns: IoT cameras and microphones capture audio and video data within your home, raising privacy concerns. Be mindful of where and how you place these devices, ensuring they do not invade the private spaces of your household or disclose sensitive information inadvertently.
2. Secure Access Credentials: Ensure that your IoT-enabled cameras and microphones are protected with strong and unique passwords to prevent unauthorized access. Change default credentials immediately upon installation and avoid using easily guessable passwords or personal information.
3. Regular Firmware Updates: Keep your IoT devices firmware up to date with the latest patches and security updates provided by the manufacturer. These updates address potential vulnerabilities and help ensure that your devices are protected from known threats.
4. Check Manufacturer Reputation: Research the reputation and security practices of manufacturers before purchasing IoT-enabled cameras and microphones. Choose devices from reputable brands that prioritize security, issue regular updates, and promptly address reported vulnerabilities.
5. Secure Your Home Network: Ensure that your home network, including Wi-Fi routers and firewalls, is properly secured. Use strong passwords and encryption protocols, and regularly update firmware to protect against potential attacks on your IoT devices.
6. Disable Remote Access Features: Evaluate whether you truly need remote access to your cameras and microphones. If remote access is not essential for your use case, consider disabling this feature to minimize potential security risks associated with remote access vulnerabilities.
7. Encrypt Data Transmissions: Use encryption protocols and secure communication channels to transmit data captured by IoT cameras and microphones. Encryption ensures that the data is protected from interception during transmission, even if someone gains unauthorized access to your network.
8. Regularly Monitor Device Activity: Periodically review the activity logs and settings of your IoT cameras and microphones, looking for any suspicious or unexpected behavior. Regular monitoring allows you to detect any unauthorized access attempts or unusual activity and respond promptly.
9. Physical Security: Secure the physical placement of your IoT cameras and microphones to prevent tampering or unauthorized access. Ensure that they are mounted or positioned in areas where they capture the desired view while minimizing the risk of being easily interfered with by outsiders.
10. Opt-Out of Data Sharing: Check the devices privacy settings and understand the data sharing practices of the manufacturer. If available, opt-out of data sharing arrangements to maintain better control over the privacy and security of your captured audio and video data.
By exercising caution and implementing these best practices, you can minimize privacy risks and enhance the security of your IoT-enabled cameras and microphones. Taking proactive measures helps ensure that you can enjoy the benefits of these devices while maintaining control over your privacy and maintaining a secure smart home ecosystem.
Protect Your Smart Home from Physical Intrusion
While securing your smart home devices from cyber threats is crucial, its equally important to implement measures to protect your smart home from physical intrusion. Physical security ensures that unauthorized individuals cannot gain physical access to your devices or tamper with your smart home ecosystem. Here are key steps to protect your smart home from physical intrusion:
1. Secure Physical Access Points: Strengthen the security of your doors, windows, and any other entry points to your home. Use sturdy locks and deadbolts, reinforce windows with security film or bars, and consider installing smart locks or security systems that provide monitoring and alerts.
2. Install Security Cameras: Strategically place security cameras both indoors and outdoors to monitor and record any suspicious activity. Ensure that the camera footage is encrypted and stored securely to protect your privacy and provide evidence in case of a security breach.
3. Implement Motion Sensors and Alarms: Install motion sensors and alarms that detect movement and potential intruders. Link these sensors with your smart home hub to trigger alerts or notifications whenever unauthorized activity is detected.
4. Set up Smart Doorbells: Smart doorbells provide video and audio communication, allowing you to remotely see and speak to visitors at your doorstep. They also often include motion detection and recording capabilities, enhancing the security of your homes entry points.
5. Use Smart Lighting: Utilize smart lighting features to create the illusion of someone being home by automating lights to turn on and off at specific times or when triggered by motion sensors. This deters potential intruders who may be monitoring your home for periods of inactivity.
6. Create a Neighborhood Watch: Get to know your neighbors and establish a community watch program. Neighbors can help keep an eye on each others homes, report suspicious activities, and collaborate on implementing security measures to enhance the overall safety of your neighborhood.
7. Employ Secure Storage for Valuables: Use secure storage solutions, such as safes or lockboxes, to protect your valuables, important documents, and backup storage devices. This provides an extra layer of protection against physical theft and ensures that critical data remains secure even if the devices are stolen.
8. Avoid Sharing Sensitive Information: Be cautious about sharing sensitive information about your smart home devices, such as brand names or specific models, to minimize the risk of targeted attacks or easy identification of vulnerable entry points.
9. Educate Household Members: Ensure that everyone in your household understands the importance of physical security. Educate them about security practices, such as locking doors and windows, setting alarms, and being cautious when sharing access codes or keys.
10. Develop an Emergency Response Plan: Establish a plan for responding to physical security breaches, including how to safely evacuate and contact authorities. Regularly review and rehearse this plan with all household members to ensure preparedness in case of emergencies.
By implementing these physical security measures, you can significantly enhance the protection of your smart home. Coupled with cybersecurity practices, physical security measures play a vital role in ensuring the overall safety and security of your smart home ecosystem.
Be Aware of Cybersecurity Best Practices
Maintaining cybersecurity best practices is essential for ensuring the safety and integrity of your smart home ecosystem. By following these practices, you can minimize the risk of cyber threats and protect your devices, data, and privacy. Here are some key cybersecurity best practices to keep in mind:
1. Strong Passwords: Use strong and unique passwords for all your smart home devices, Wi-Fi network, and online accounts. Avoid using easily guessable passwords and consider using a password manager to securely store and generate complex passwords.
2. Multi-Factor Authentication (MFA): Enable multi-factor authentication whenever possible. MFA adds an extra layer of security by requiring additional verification, such as a unique code sent to your mobile device, in addition to your password.
3. Regularly Update Software and Firmware: Keep your smart home devices, routers, and applications up to date with the latest software and firmware updates. Updates often contain security patches that address known vulnerabilities.
4. Secure Wi-Fi Network: Use strong encryption protocols, such as WPA2 or WPA3, for your Wi-Fi network. Change the default network name (SSID) and set a strong, unique password to prevent unauthorized access to your network.
5. Use Secure Networks: Be cautious when connecting your smart devices to public Wi-Fi networks. Only use trusted and secure networks to minimize the risk of data interception and unauthorized access to your devices.
6. Regularly Backup Data: Regularly back up your important data, including device configurations and settings, to prevent the loss of critical information in case of a security breach or device failure. Store backups securely, preferably offline or in the cloud with strong encryption.
7. Employ Network Segmentation: Implement network segmentation to separate your smart home devices from personal computers and other devices. This practice minimizes the potential impact of a breach and contains any malicious activity to a specific network segment.
8. Be Wary of Suspicious Emails and Phishing: Exercise caution when opening emails, particularly those from unknown senders or with suspicious attachments or links. Be vigilant to avoid falling victim to phishing attempts that may compromise your smart home security.
9. Regularly Monitor Device Activity: Routinely review the activity logs and settings of your smart home devices. Check for any unusual or unexpected behavior that may indicate potential security breaches or unauthorized access. Promptly investigate and address any anomalies.
10. Stay Informed and Educated: Stay updated on the latest cybersecurity threats, trends, and best practices. Keep yourself informed about the security features of your devices and regularly educate yourself and your household members about potential risks and security measures.
By adhering to these cybersecurity best practices, you can maintain a robust defense against cyber threats and ensure the continued security of your smart home ecosystem. Regularly review and reinforce these practices to adapt to emerging threats and evolving cybersecurity landscape.
Conclusion
Securing your smart home devices is essential to protect your privacy, data, and the overall integrity of your smart home ecosystem. By implementing the best practices outlined in this article, you can significantly enhance the security of your smart home devices and minimize the risk of cyber threats.
From choosing secure devices and keeping them updated to creating strong passwords, enabling two-factor authentication, and securing your Wi-Fi network, each step plays a crucial role in safeguarding your smart home. Disabling unnecessary features and being cautious of IoT-enabled cameras and microphones further strengthens your defense against potential intrusions.
Physical security measures such as securing access points, installing security cameras, and implementing motion sensors add an extra layer of protection against physical breaches. Additionally, following cybersecurity best practices and staying informed about the latest threats help you remain one step ahead of potential vulnerabilities.
Remember that securing your smart home is an ongoing process. Regularly review and update your security measures, apply firmware updates, and stay vigilant for emerging threats. By doing so, you can enjoy the convenience and comfort of your smart home while ensuring a high level of security.
Take the time to assess your current smart home setup, prioritize security, and implement the necessary measures. By taking proactive steps to secure your smart home, you can create a safe and protected environment for you and your family.