Building a Career in Ethical Hacking Utilizing Penetration Testing Techniques to Identify Network Vulnerabilities
MakeUseOf
To catch a criminal, you must think like one by understanding the tactics and patterns of the criminal.
Ethical hackers are the opposite of cybercriminals. As an ethical hacker, you'll be working around the clock to nullify the efforts of the bad buys trying to breach computer networks.
So, what skills do you need to become an ethical hacker? Where can you learn ethical hacking? And what are the entry-level jobs for ethical hacking? You are about to find out.
What Skills Do You Need for Ethical Hacking?
There are two major types of hackersmalicious (black hat) hackers and ethical (white hat) hackers. The difference between black and white hat hackers is in the intention. Malicious hacking is the unauthorized process of gaining illegal access to data and systems. On the other hand, ethical hacking is the authorized process of detecting vulnerabilities in an application or system by employing hacking techniques to identify potential loopholes.
To be successful in the field of ethical hacking, you need the following skills:
1. Hardware Knowledge
Hardware knowledge refers to the physical features and functions of a computer system.
As an ethical hacker, you must be conversant with features such as Visual Display Unit (VDU), Central Processing Unit (CPU), keyboard, hard drive, speakers, sound card, mouse, graphics card, and motherboard.
2. Basic and Advanced Computer Skills
Computer skills lay the foundation for ethical hacking. Possessing basic computer skills like data processing, managing computer files, and creating presentations help you use computers easily.
But since an ethical hacker is a cybersecurity expert, basic computer skills aren't enough. You need to possess advanced computer skills to be well-grounded on the job. Such advanced computer skills include programming, coding, managing databases, etc.
3. Thorough Computer Networking Skills
A vital prerequisite to being an efficient ethical hacker is having a very sound and well-rounded knowledge of computer networks.
Hacking involves the penetration and exploitation of computer systems and networks. Thus, an aspiring ethical hacker must understand the use of networking commands such as OSI models, IP addresses, MAC addresses, subnetting, and routing.
4. Expert Knowledge of Operating Systems
To build a successful career in ethical hacking, you need a strong knowledge of operating systems like Ubuntu, Linux, Red Hat, etc.
Linux is a very popular operating system among web servers. As an aspiring ethical hacker, you can start with mastering the Linux programming system and then broaden your skills in others over time.
5. Programming Language Skills
The language computer systems understand is presented in binary formats called codes. These codes are written in various programming languages such as Java, Javascript, SQL, Bash, Python, C, C++, Ruby, Perl, and PHP.
As an ethical hacker, you must learn these programming languages and have excellent programming skills.
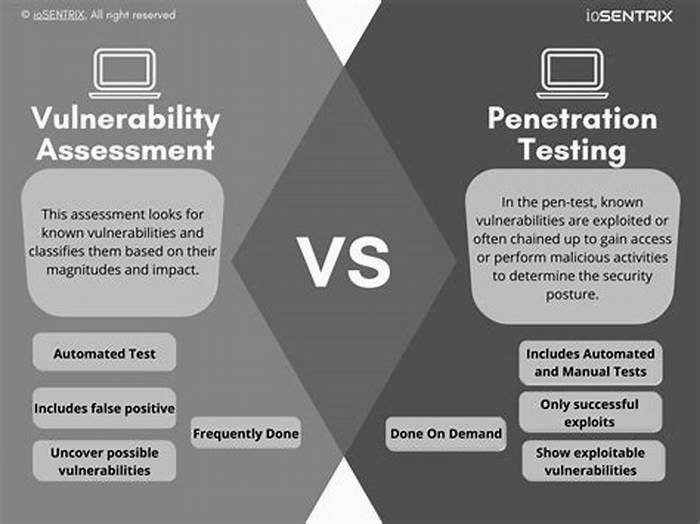
A successful ethical hacker must be an expert in penetration testing. And that's because they need to penetrate networks to detect loopholes and create more robust security frameworks.
You have to be knowledgeable about the various penetration testing methodologies to identify the most suitable ones in any given situation.
7. Cybersecurity Skills
Cybersecurity is at the core of ethical hacking. To keep cybercriminals at bay, you must understand the necessary cybersecurity techniques and how to implement them.
The cybersecurity techniques you need to learn include phishing, man-in-the-middle attacks, app protection, device hardware protectors, database management systems, spyware, password systems, etc.
How to Start Learning Ethical Hacking
The globally accepted ethical hacking certification is Certified Ethical Hacker (CEH). However, various platforms teach aspiring ethical hackers the skills they need to thrive in the profession. Let's look at some of them.
Cybrary is a leading IT and cybersecurity professional development platform with extensive training on cybersecurity and verifiable ethical hacking certifications.
StationX is a global leader in cybersecurity. It prepares you for in-demand industry certifications with courses tied directly to the learning objective.
EH Academy offers ethical hacking courses, covering penetration tools like Nmap, Metasploit, and advanced commands like Linux.
If you already have a basic knowledge of IT and cybersecurity, EH Academy offers a wide range of advanced specialized ethical hacking courses like Metasploit training for penetration testing, python for offensive penetration testing, advanced mobile applications testing, and VoIP hacking.
Offensive Security offers specialized training on Metasploit. The institution claims to offer the most complete and in-depth Metasploit guide. It's a good starting point for information security professionals who want to learn penetration testing.
What Are the Entry-Level Jobs in Ethical Hacking?
The field of ethical hacking offers various job opportunities for beginners. If you have made up your mind to become a certified ethical hacker, here are some entry-level roles to start your ethical hacking career.
1. Cyber Mission Specialist
The role of a cyber mission specialist is to design, plan, execute, report and sanitize in a cyber range environment.
The cyber mission specialist identifies and leads market development opportunities in cyberspace. The personnel leverage domain knowledge to create cybersecurity solutions that align with a client's mission, applying leading-edge principles, theories, concepts, and tools.
2. Associate Tech Programmer
An associate tech programmer works with staff and clients to develop and enhance applications, programs, and scripts that ensure efficient maintenance of all programming logic, codes, and commands aligned with the company's standards.
3. Junior Systems Engineer
As a junior systems engineer, your job is to help develop and maintain all computer systems and make them ready and secure for business. You are responsible for supporting the IT department in maintaining the stability and efficiency of network servers and systems.
The junior systems engineer is involved in installing, monitoring, and troubleshooting operating systems. They execute the development of potent hardware and software infrastructures.
4. Information Security Analyst
An information security analyst monitors an organization's networks and looks out for incoming security breaches. They are the first responders to investigate such breaches when they occur.
The information security analyst implements applications such as digital firewalls and data encryption programs to secure and protect confidential information.
5. Mobile Vulnerability Analyst
Mobile vulnerability analysts are responsible for performing vulnerability assessments of mobile applications using high-end cybersecurity tools and techniques.
The mobile vulnerability analyst identifies opportunities for future research projects involving mobile applications and communications. They utilize hacking and penetration test techniques to target mobile apps and web services that run on mobile devices. They are responsible for the API security on endpoints in the mobile application architecture.
6. Information Security Engineer
The information security engineer shares similarities with the junior systems engineer. The difference is that, while the junior systems engineer's role primarily targets computer systems and networks, the information security engineer is mainly concerned with securing data.
The information security engineer plans, designs, builds, and integrates tools that protect electronic information. They develop and implement systems to collect information about security incidents and outcomes.
7. Cloud Security Engineer
A cloud security engineer's role is to identify potential threats and attacks to cloud systems and develop new features to meet cloud security needs by building and maintaining upgrades and continuously improving their cloud-based platforms/systems.
The cloud security engineer analyzes and investigates existing cloud-system structures and creates proactive measures through enhanced cybersecurity methods.
What Is the Career Progression in Ethical Hacking?
Your career growth as a certified ethical hacker depends heavily on the right mentorship, cybersecurity skills, years of experience, and a track record of verifiable cybersecurity results.
The ethical hacking profession is more results-driven rather than effort-motivated. Being a part of an elite cybersecurity team is another step toward a sustained progression in your ethical hacking career.
Securing Cyber Assets as an Ethical hacker
The increased reliance and dependence on digital applications have made us vulnerable to cyberattacks. Hence, ethical hacking is a proactive cybersecurity measure to protect networks and systems from cyber threats.
As an expert certified ethical hacker, you need the right skills and exposure to be several steps ahead of the malicious hacker. Understanding the strengths and weaknesses of the enemy is a great way to defeat them. Your greatest achievement is being their biggest nemesis as you secure cyber assets.
Network Penetration Testing and Ethical Hacking
As a cybersecurity professional, you have a unique responsibility to find and understand your organization's vulnerabilities and to work diligently to mitigate them before the bad guys pounce. Are you ready? SEC560, the flagship SANS course for penetration testing, fully arms you to address this duty head-on.
SEC560 IS THE MUST-HAVE COURSE FOR EVERY WELL-ROUNDED SECURITY PROFESSIONAL
With comprehensive coverage of tools, techniques, and methodologies for network penetration testing, SEC560 truly prepares you to conduct high-value penetration testing projects step by step and end to end. Every organization needs skilled information security personnel who can find vulnerabilities and mitigate their effects, and this entire course is specially designed to get you ready for that role. The course starts with proper planning, scoping and recon, then dives deep into scanning, target exploitation, password attacks, and web app manipulation, with over 30 detailed hands-on labs throughout. The course is chock full of practical, real-world tips from some of the world's best penetration testers to help you do your job safely, efficiently...and with great skill.
LEARN THE BEST WAYS TO TEST YOUR OWN SYSTEMS BEFORE THE BAD GUYS ATTACK
You'll learn how to perform detailed reconnaissance, studying a target's infrastructure by mining blogs, search engines, social networking sites, and other Internet and intranet infrastructures. Our hands-on labs will equip you to scan target networks using best-of-breed tools. We won't just cover run-of-the-mill options and configurations, we'll also go over the lesser-known but super-useful capabilities of the best pen test toolsets available today. After scanning, you'll learn dozens of methods for exploiting target systems to gain access and measure real business risk. You'll dive deep into post-exploitation, password attacks, and web apps, pivoting through the target environment to model the attacks of real-world bad guys to emphasize the importance of defense in depth.
EQUIPPING SECURITY ORGANIZATIONS WITH COMPREHENSIVE PENETRATION TESTING AND ETHICAL HACKING KNOW-HOW
SEC560 is designed to get you ready to conduct a full-scale, high-value penetration test and at the end of the course you'll do just that. After building your skills in comprehensive and challenging labs, the course culminates with a final real-world penetration test scenario. You'll conduct an end-to-end pen test, applying knowledge, tools, and principles from throughout the course as you discover and exploit vulnerabilities in a realistic sample target organization, demonstrating the skills you've gained in this course.
Ethical Hacking Essentials (EHE)
Ethical Hacking Essentials is an introductory cybersecurity course that covers ethical hacking and penetration testing fundamentals and prepares learners for a career in cybersecurity. This course will introduce learners to computer and network security concepts such as threats and vulnerabilities, password cracking, web application attacks, IoT and OT attacks, cloud computing, pentesting fundamentals, and more.
This course provides hands-on practical experience to learners thus giving them the skills necessary for a future in cybersecurity.EHE-certified learners have an assured means of formal recognition to add to their resumes and show off their expertise and skills to prospective employers. This improves their prospects for employment advancement, higher salaries, and greater job satisfaction.