Building a Career in Cybersecurity Tech Gear Used by Ethical Hackers
What Is Ethical Hacking?
Ethical hacking is the practice of performing security assessments using the same techniques that hackers use, but with proper approvals and authorisation from the organisation you're hacking into. The goal is to use cybercriminals tactics, techniques, and strategies to locate potential weaknesses and reinforce an organisations protection from data and security breaches.
Cybersecurity Ventures predicts that cybercrime will globally cost an estimated $10.5 trillion every year in damages by 2025 [1]. It also predicts that ransomware alone will cost victims $265 billion every year by 2031. In this article, explore key points to consider if youre thinking of going into ethical hacking.
Ethical hacking vs. hacking: Whats the difference?
Hackers, who are often referred to as black-hat hackers, are those known for illegally breaking into a victims networks. Their motives are to disrupt systems, destroy or steal data and sensitive information, and engage in malicious activities or mischief.
Black-hat hackers usually have advanced knowledge for navigating around security protocols, breaking into computer networks, and writing the malware that infiltrates systems. Here are some of the differences:
Ethical hackers, commonly called white-hat hackers, use many of the same skills and knowledge as black-hat hackers but with the approval of the company that hires them. These information security professionals are hired specifically to help find and secure vulnerabilities that may be susceptible to a cyber attack. Ethical hackers will regularly engage in assessing systems and networks and reporting those findings.
| Ethical hackers | Black-hat hackers |
|---|---|
| Increase security framework | Reduce security and steal data |
| Develop strong security and structures | Access accounts and data without permission |
| Develop systems like ad blockers and firewalls and regularly update and maintain security systems | Steal valuable data and break into restricted data areas |
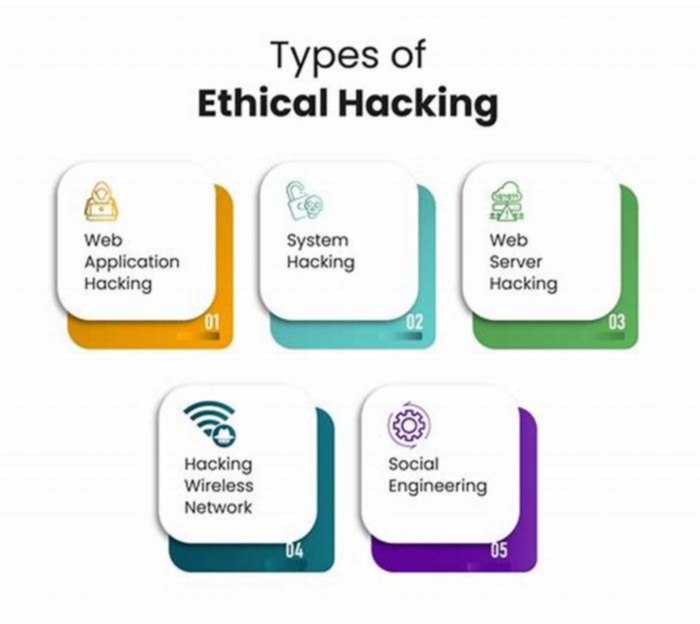
Types of hackers
Black-hat hackers are those with malicious intentions.
Within ethical hacking, there are a variety of roles other than white-hat hackers. Some of the roles include red teams that work in an offensive capacity, blue teams that work as a defense for security services, and purple teams that do a little of both:
Blue teams are aware of the business objectives and security strategy of the organisation they work for. They gather data, document the areas that need protection, conduct risk assessments, and strengthen the defenses to prevent breaches. These ethical hackers may introduce stronger password policies, limit access to the system, put monitoring tools in place, and educate other staff members so that everyone's on the same page.
Benefits of ethical hacking
New viruses, malware, ransomware, and worms emerge all the time, underscoring the need for ethical hackers to help safeguard the networks belonging to government agencies, defense departments, and businesses. The main benefit of ethical hacking is reducing the risk of data theft. Additional benefits include:
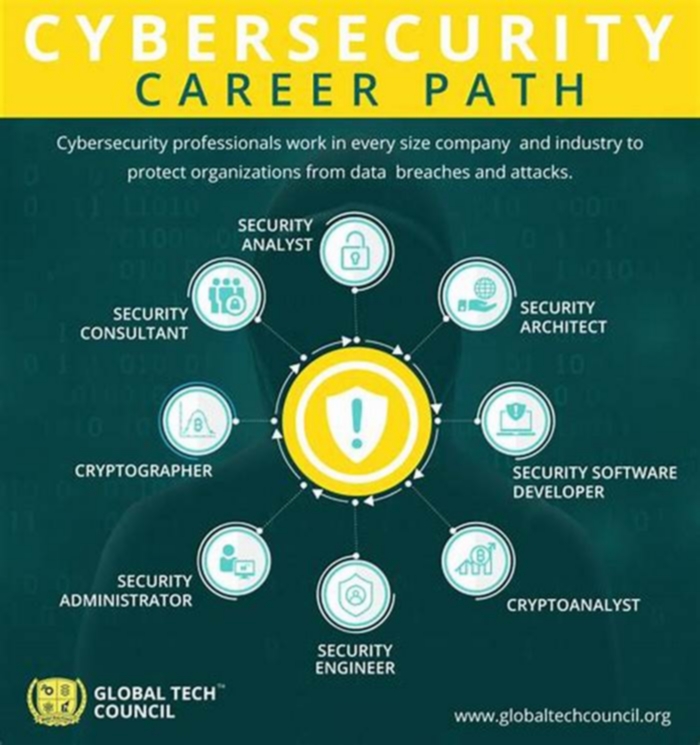
Job opportunities for ethical hackers
As an ethical hacker, you might work as a full-time employee or as a consultant. You could find a job in nearly any type of organisation, including public, private, and government institutions. You could work in financial institutions like banks or payment processors. Other potential job areas include e-commerce marketplaces, data centers, cloud computing companies, entertainment companies, media providers, and SaaS companies. Some common job titles you'll find within the ethical hacking realm include:
Ethical hacker salary
The national average base salary for an ethical hacker in the UK was 52,285 in April 2023, according to Glassdoor [2].
Steps to become an ethical hacker
Theres no single degree you have to pursue to become an ethical hacker, but having a strong background of experience and expertise is a must. Many ethical hackers earn a university degree at a minimum. Gaining certifications can boost your credibility with potential clients and employers and increase your earning potential.
Pursue a degree.
Many ethical hackers start with at least a bachelors degree. While there is no one particular area of study you must pursue, useful subjects can include computer science or information systems, maths, physics or other science subjects. You might also pursue a master's degree in cybersecurity.
Expand your skills.
If you already have a degree but want to pivot to gain skills in ethical hacking, you might attend an ethical hacking or cybersecurity bootcamp. Employers generally look for individuals who can demonstrate:
Experience with programming languages
Skills in scripting to deal with network-based and host-based attacks.
Understanding of how networks are connected and how to handle network compromise situations
Knowledge of databases like SQL and multiple operating systems like Windows, Linux, Mac
Get Certified.
One of the core certifications to consider is the Certified Ethical Hacker credential issued by the EC-Council. Other popular certifications include:
CompTIA Security+ covers a broad range of knowledge about troubleshooting and problem-solving a variety of issues, including networking, mobile devices, and security.
Next steps
Prepare to launch your career in cybersecurity with the Google Cybersecurity Professional Certificate on Coursera. Get hands-on experience with industry tools and examine real-world case studies, all at your own pace. Upon completion, youll have a certificate for your resume and be prepared to explore job titles like security analyst, SOC (security operations center) analyst, and more.
MakeUseOf
To catch a criminal, you must think like one by understanding the tactics and patterns of the criminal.
Ethical hackers are the opposite of cybercriminals. As an ethical hacker, you'll be working around the clock to nullify the efforts of the bad buys trying to breach computer networks.
So, what skills do you need to become an ethical hacker? Where can you learn ethical hacking? And what are the entry-level jobs for ethical hacking? You are about to find out.
What Skills Do You Need for Ethical Hacking?
There are two major types of hackersmalicious (black hat) hackers and ethical (white hat) hackers. The difference between black and white hat hackers is in the intention. Malicious hacking is the unauthorized process of gaining illegal access to data and systems. On the other hand, ethical hacking is the authorized process of detecting vulnerabilities in an application or system by employing hacking techniques to identify potential loopholes.
To be successful in the field of ethical hacking, you need the following skills:
1. Hardware Knowledge
Hardware knowledge refers to the physical features and functions of a computer system.
As an ethical hacker, you must be conversant with features such as Visual Display Unit (VDU), Central Processing Unit (CPU), keyboard, hard drive, speakers, sound card, mouse, graphics card, and motherboard.
2. Basic and Advanced Computer Skills
Computer skills lay the foundation for ethical hacking. Possessing basic computer skills like data processing, managing computer files, and creating presentations help you use computers easily.
But since an ethical hacker is a cybersecurity expert, basic computer skills aren't enough. You need to possess advanced computer skills to be well-grounded on the job. Such advanced computer skills include programming, coding, managing databases, etc.
3. Thorough Computer Networking Skills
A vital prerequisite to being an efficient ethical hacker is having a very sound and well-rounded knowledge of computer networks.
Hacking involves the penetration and exploitation of computer systems and networks. Thus, an aspiring ethical hacker must understand the use of networking commands such as OSI models, IP addresses, MAC addresses, subnetting, and routing.
4. Expert Knowledge of Operating Systems
To build a successful career in ethical hacking, you need a strong knowledge of operating systems like Ubuntu, Linux, Red Hat, etc.
Linux is a very popular operating system among web servers. As an aspiring ethical hacker, you can start with mastering the Linux programming system and then broaden your skills in others over time.
5. Programming Language Skills
The language computer systems understand is presented in binary formats called codes. These codes are written in various programming languages such as Java, Javascript, SQL, Bash, Python, C, C++, Ruby, Perl, and PHP.
As an ethical hacker, you must learn these programming languages and have excellent programming skills.
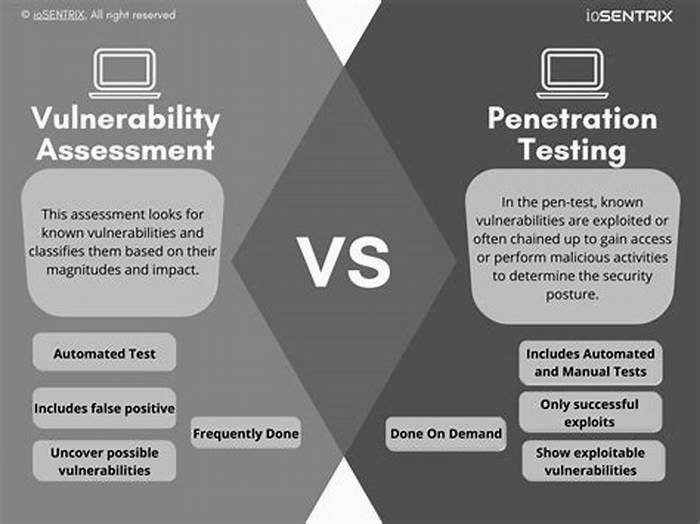
A successful ethical hacker must be an expert in penetration testing. And that's because they need to penetrate networks to detect loopholes and create more robust security frameworks.
You have to be knowledgeable about the various penetration testing methodologies to identify the most suitable ones in any given situation.
7. Cybersecurity Skills
Cybersecurity is at the core of ethical hacking. To keep cybercriminals at bay, you must understand the necessary cybersecurity techniques and how to implement them.
The cybersecurity techniques you need to learn include phishing, man-in-the-middle attacks, app protection, device hardware protectors, database management systems, spyware, password systems, etc.
How to Start Learning Ethical Hacking
The globally accepted ethical hacking certification is Certified Ethical Hacker (CEH). However, various platforms teach aspiring ethical hackers the skills they need to thrive in the profession. Let's look at some of them.
Cybrary is a leading IT and cybersecurity professional development platform with extensive training on cybersecurity and verifiable ethical hacking certifications.
StationX is a global leader in cybersecurity. It prepares you for in-demand industry certifications with courses tied directly to the learning objective.
EH Academy offers ethical hacking courses, covering penetration tools like Nmap, Metasploit, and advanced commands like Linux.
If you already have a basic knowledge of IT and cybersecurity, EH Academy offers a wide range of advanced specialized ethical hacking courses like Metasploit training for penetration testing, python for offensive penetration testing, advanced mobile applications testing, and VoIP hacking.
Offensive Security offers specialized training on Metasploit. The institution claims to offer the most complete and in-depth Metasploit guide. It's a good starting point for information security professionals who want to learn penetration testing.
What Are the Entry-Level Jobs in Ethical Hacking?
The field of ethical hacking offers various job opportunities for beginners. If you have made up your mind to become a certified ethical hacker, here are some entry-level roles to start your ethical hacking career.
1. Cyber Mission Specialist
The role of a cyber mission specialist is to design, plan, execute, report and sanitize in a cyber range environment.
The cyber mission specialist identifies and leads market development opportunities in cyberspace. The personnel leverage domain knowledge to create cybersecurity solutions that align with a client's mission, applying leading-edge principles, theories, concepts, and tools.
2. Associate Tech Programmer
An associate tech programmer works with staff and clients to develop and enhance applications, programs, and scripts that ensure efficient maintenance of all programming logic, codes, and commands aligned with the company's standards.
3. Junior Systems Engineer
As a junior systems engineer, your job is to help develop and maintain all computer systems and make them ready and secure for business. You are responsible for supporting the IT department in maintaining the stability and efficiency of network servers and systems.
The junior systems engineer is involved in installing, monitoring, and troubleshooting operating systems. They execute the development of potent hardware and software infrastructures.
4. Information Security Analyst
An information security analyst monitors an organization's networks and looks out for incoming security breaches. They are the first responders to investigate such breaches when they occur.
The information security analyst implements applications such as digital firewalls and data encryption programs to secure and protect confidential information.
5. Mobile Vulnerability Analyst
Mobile vulnerability analysts are responsible for performing vulnerability assessments of mobile applications using high-end cybersecurity tools and techniques.
The mobile vulnerability analyst identifies opportunities for future research projects involving mobile applications and communications. They utilize hacking and penetration test techniques to target mobile apps and web services that run on mobile devices. They are responsible for the API security on endpoints in the mobile application architecture.
6. Information Security Engineer
The information security engineer shares similarities with the junior systems engineer. The difference is that, while the junior systems engineer's role primarily targets computer systems and networks, the information security engineer is mainly concerned with securing data.
The information security engineer plans, designs, builds, and integrates tools that protect electronic information. They develop and implement systems to collect information about security incidents and outcomes.
7. Cloud Security Engineer
A cloud security engineer's role is to identify potential threats and attacks to cloud systems and develop new features to meet cloud security needs by building and maintaining upgrades and continuously improving their cloud-based platforms/systems.
The cloud security engineer analyzes and investigates existing cloud-system structures and creates proactive measures through enhanced cybersecurity methods.
What Is the Career Progression in Ethical Hacking?
Your career growth as a certified ethical hacker depends heavily on the right mentorship, cybersecurity skills, years of experience, and a track record of verifiable cybersecurity results.
The ethical hacking profession is more results-driven rather than effort-motivated. Being a part of an elite cybersecurity team is another step toward a sustained progression in your ethical hacking career.
Securing Cyber Assets as an Ethical hacker
The increased reliance and dependence on digital applications have made us vulnerable to cyberattacks. Hence, ethical hacking is a proactive cybersecurity measure to protect networks and systems from cyber threats.
As an expert certified ethical hacker, you need the right skills and exposure to be several steps ahead of the malicious hacker. Understanding the strengths and weaknesses of the enemy is a great way to defeat them. Your greatest achievement is being their biggest nemesis as you secure cyber assets.